THM: Friday Overtime
- Platform: TryHackMe
- Link: Friday Overtime
- Level: Medium
For this blue team challenge we need to conduct an investigation and provide answers to some questions.
After launching the provided VM we login with the credentials ericatracy:Intel321!.
Who shared the malware samples?
Right after logging in we find a document titled Urgent: Malicious Malware Artefacts Detected.
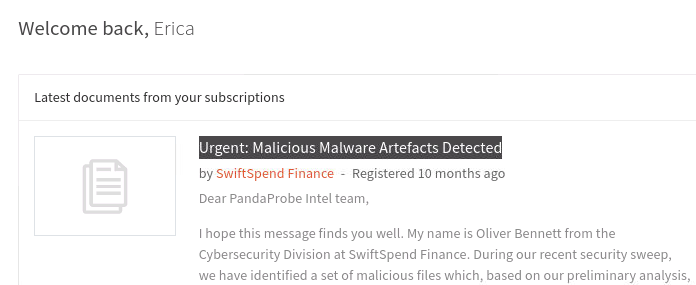
The author of the document is Oliver Bennett.
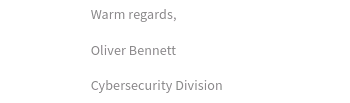
Answer: Oliver Bennett
What is the SHA1 hash of the file “pRsm.dll” inside samples.zip?
Click on Documents then on View All.
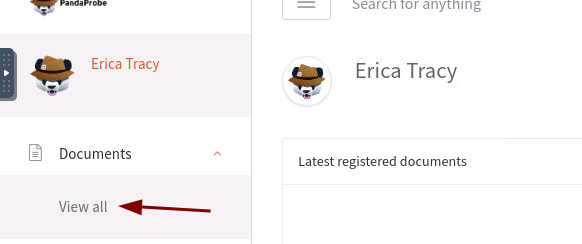
After selecting Urgent: Malicious Malware Artefacts Detected document, scroll down and you will find samples.zip on the right side.

We extract it, the password is Panda321!.
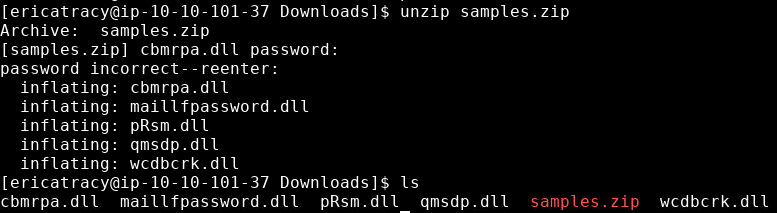
We then compute the hash of pRsm.dll.
sha1sum pRsm.dll
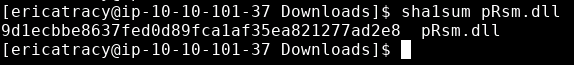
Answer: 9d1ecbbe8637fed0d89fca1af35ea821277ad2e8
Which malware framework utilizes these DLLs as add-on modules?
We compute the sha256 hash for the pRsm.dll file and search for it on VirusTotal.
2c0cfe2f4f1e7539b4700e1205411ec084cbc574f9e4710ecd4733fbf0f8a7dc
We discover the family labels attached to this file.
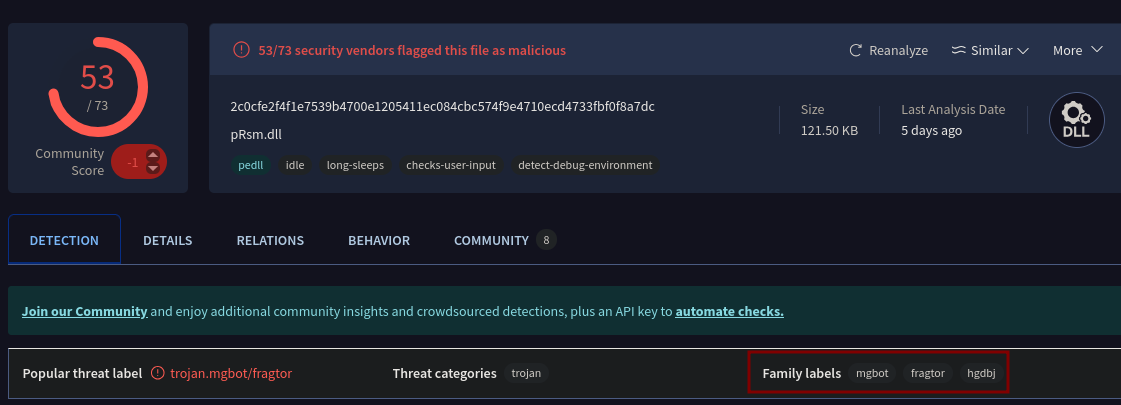
Answer: MgBot
Which MITRE ATT&CK Technique is linked to using pRsm.dll in this malware framework?
We research MITRE ATT&CK Technique pRsm.dll and find this article
.
Searching for pRsm.dll on the page we find the technique ID to be T1123
.
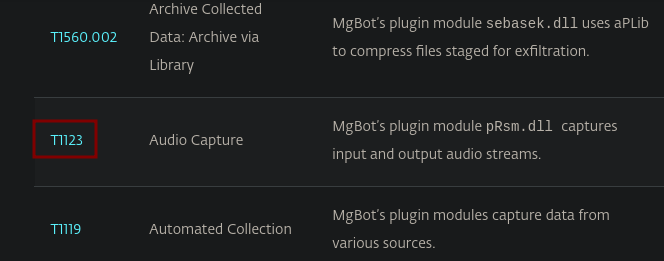
Answer: T1123
What is the CyberChef defanged URL of the malicious download location first seen on 2020-11-02?
On the same page we find an url http://update.browser.qq[.]com/qmbs/QQ/QQUrlMgr_QQ88_4296.exe.
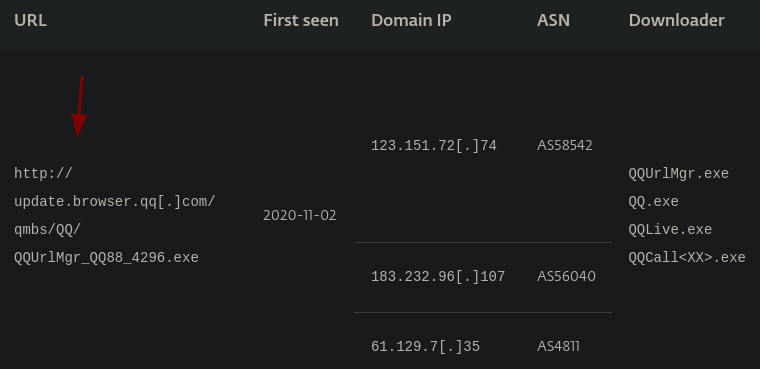
On cyberchef.org
we use the defang URL recipe to get the correct URL.
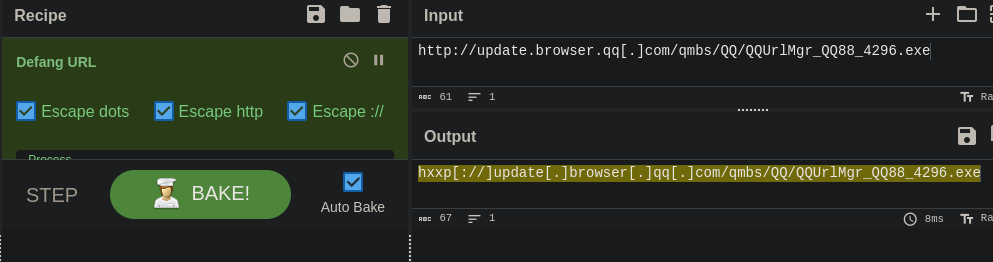
Answer: hxxp[://]update[.]browser[.]qq[.]com/qmbs/QQ/QQUrlMgr_QQ88_4296[.]exe
What is the CyberChef defanged IP address of the C&C server first detected on 2020-09-14 using these modules?
Using the same article, under the Network section we find an IP address for the specified date.
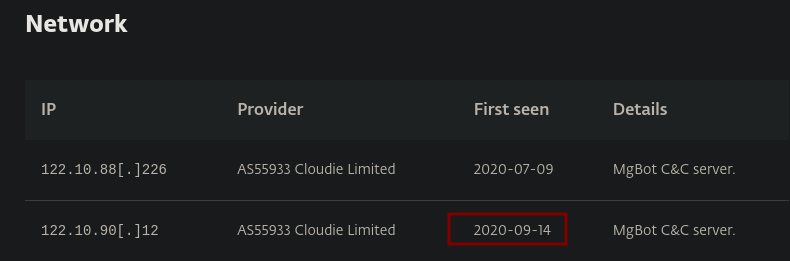
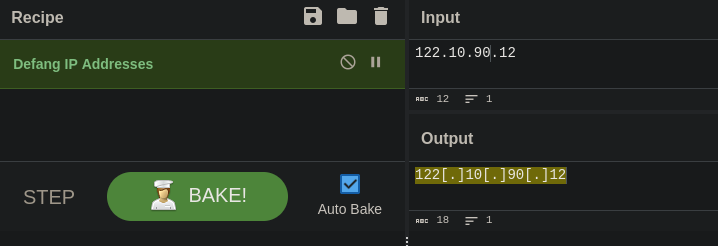
With cyberchef we get the defanged IP address with the Defang IP addresses recipe.
Answer: 122[.]10[.]90[.]12
What is the SHA1 hash of the spyagent family spyware hosted on the same IP targeting Android devices on November 16, 2022?
On VirusTotal we search for 122.10.90.12 and go to the Relations section.
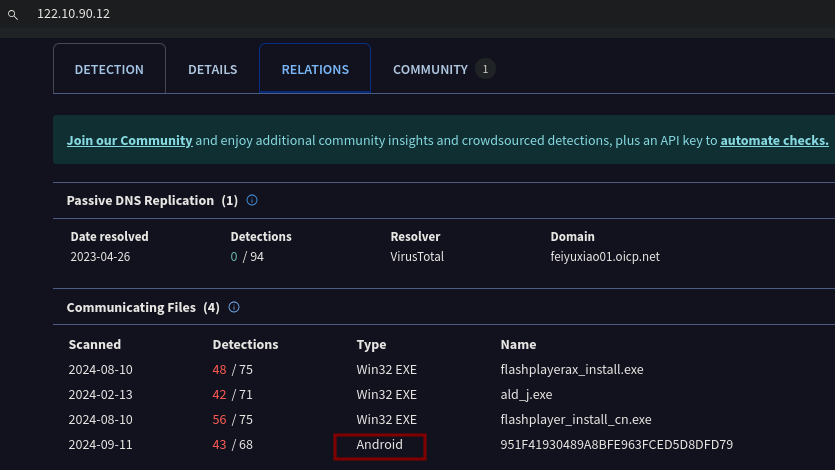
We then search for 951F41930489A8BFE963FCED5D8DFD79 and under Details we find the SHA1 hash.
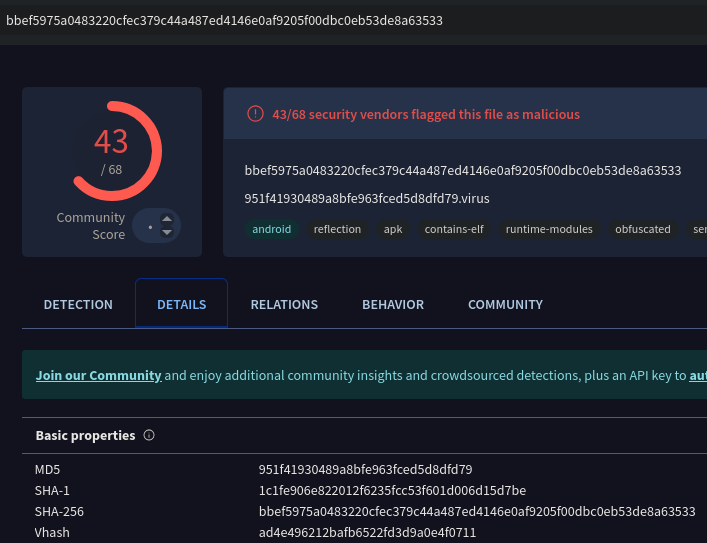
Answer: 1c1fe906e822012f6235fcc53f601d006d15d7be