THM: Summit
This is a blue team challenge where we need to create defensive countermeasures for various malware samples. This will be achieved by using file hashes, IP addresses, firewall rules, DNS and sigma rules.
- Platform: TryHackMe
- Link: Summit
- Level: Easy
What is the first flag you receive after successfully detecting sample1.exe?
After navigating to the link provided, go to Malware Snadbox, the file sample1.exe is already loaded and click on Submit for Analysis.
After the analysis is completed, we get three hash values.
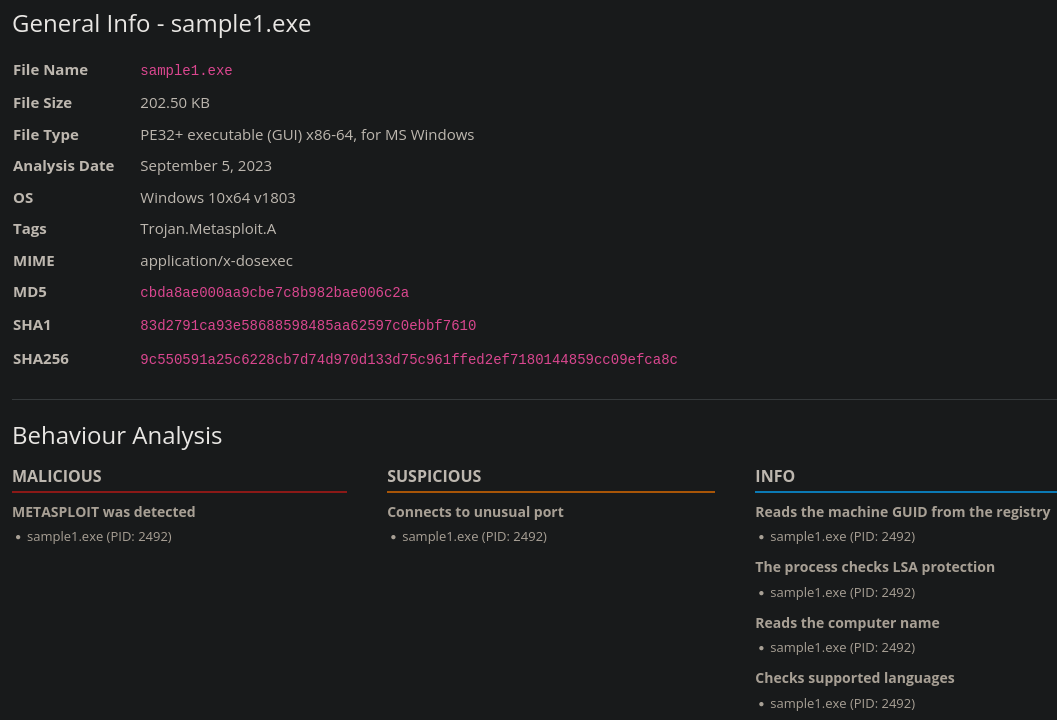
Back to the drop down menu, there is a Manage Hashes section, copy one of the hashes, check the correct Hash Algorithm box and submit it.
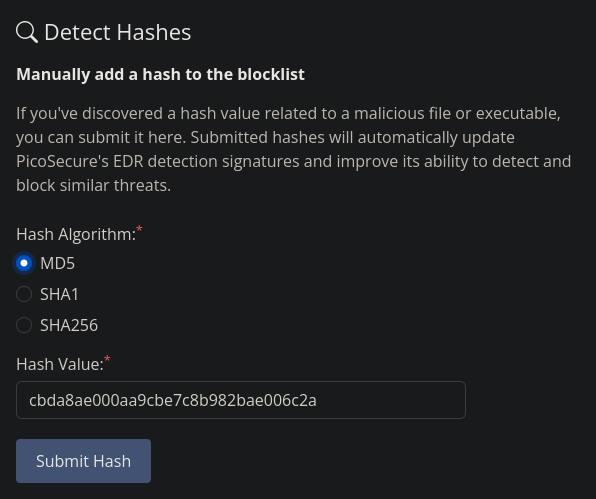
You will get some results and an email (check the Mail section in the drop down menu) with the first flag.
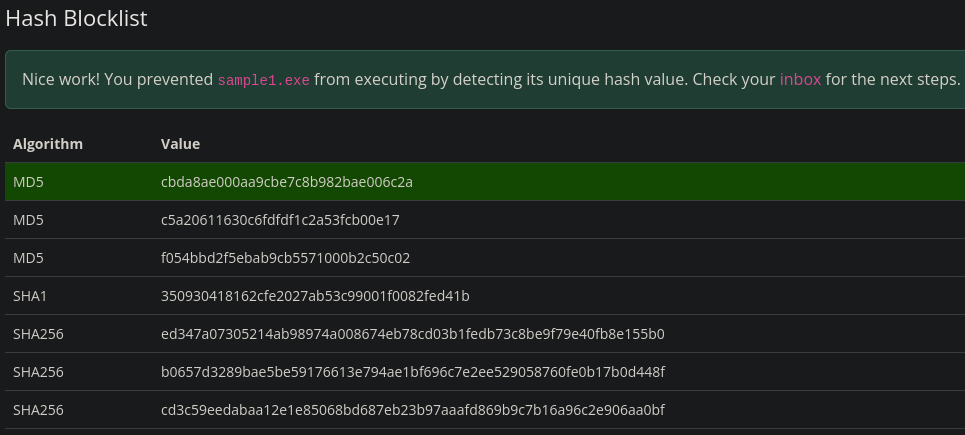
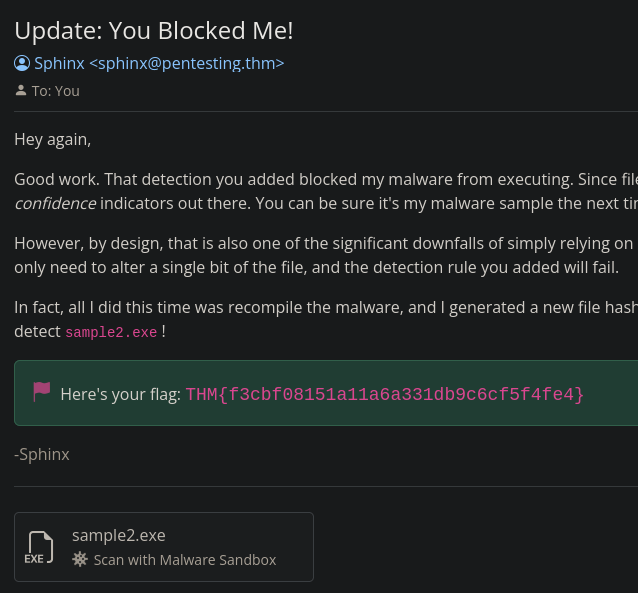
What is the second flag you receive after successfully detecting sample2.exe?
Using the same process we analyze sample2.exe. The report tells us that this file tries to send an HTTP request to IP address 154.35.10.113:4444.
If we try to get the flag via hash submission we are told that it requires another method.
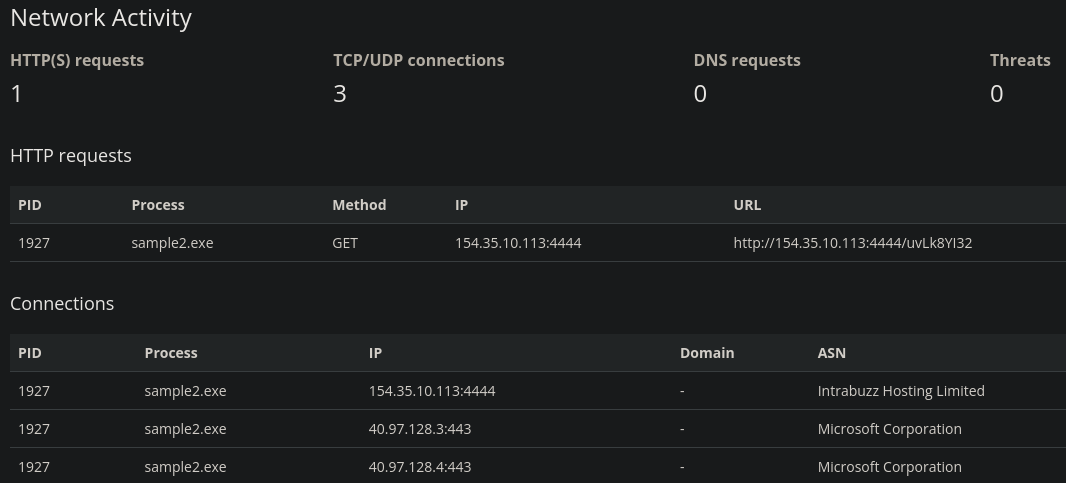
Let’s create a rule in the Firewall Rule Manager section.
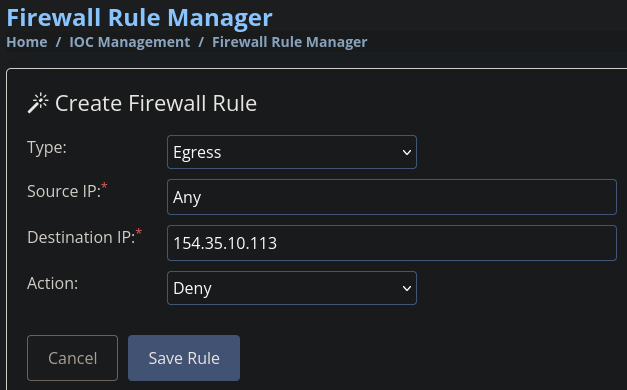
After saving that rule we get flag 2 in our mail.
What is the third flag you receive after successfully detecting sample3.exe?
After analyzing sample3.exe, we notice some HTTP requests to IP 62.123.140.9 and DNS requests to emudyn.bresonicz.info with the same IP address.
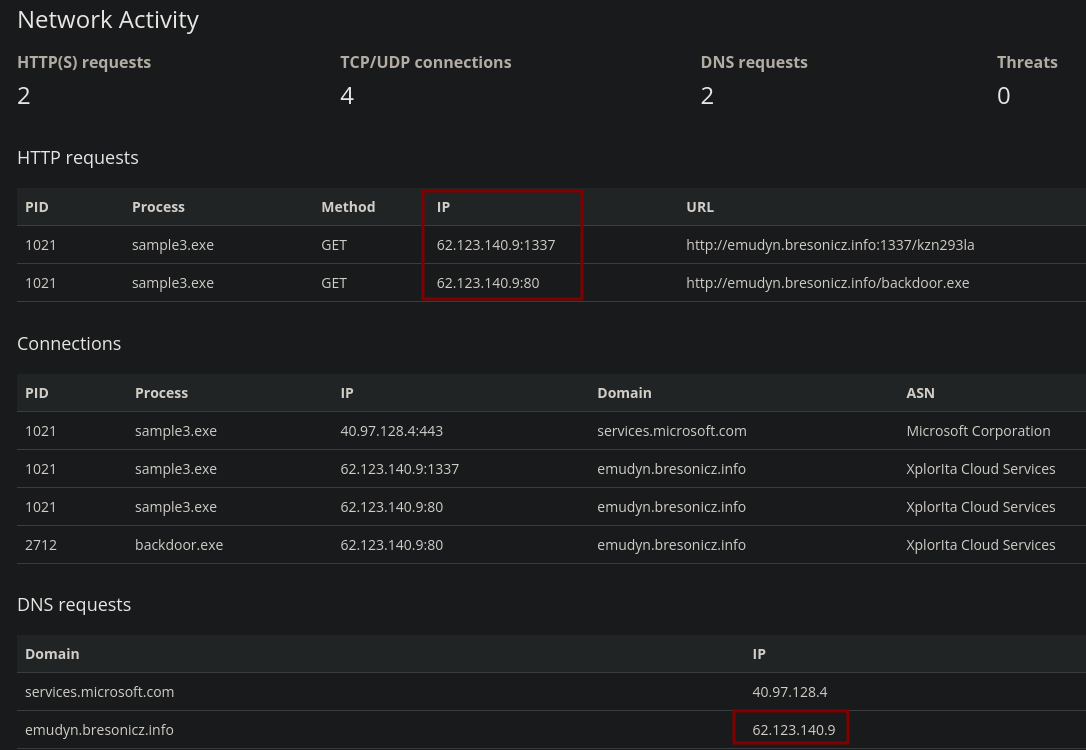
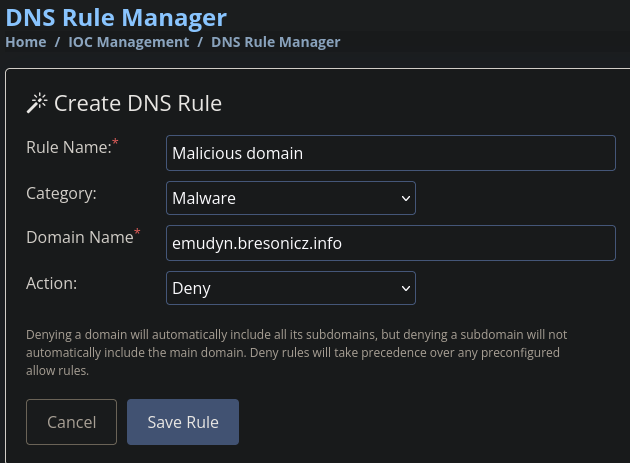
We head to the DNS Filter section and create a DNS rule for that domain which gets us the third flag.
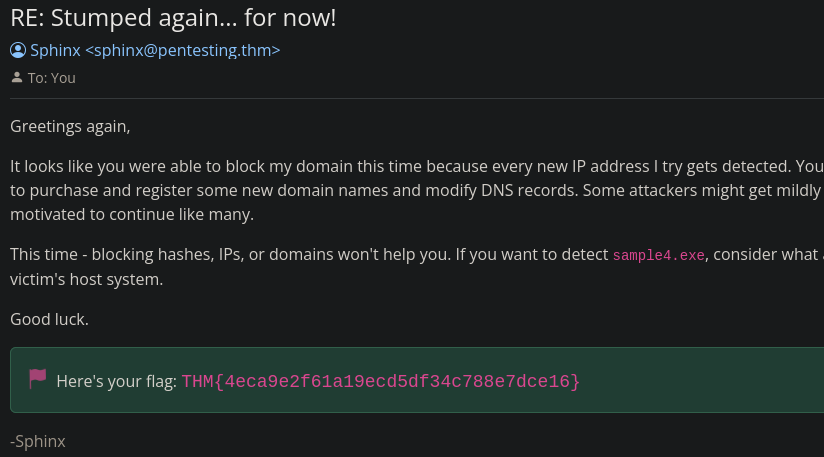
What is the fourth flag you receive after successfully detecting sample4.exe?
From the previous email, we know that blocking hashes, IPs, or domain will not solve our problem. We need to look deeper.
The analysis report of sample4.exe shows some registry activity.
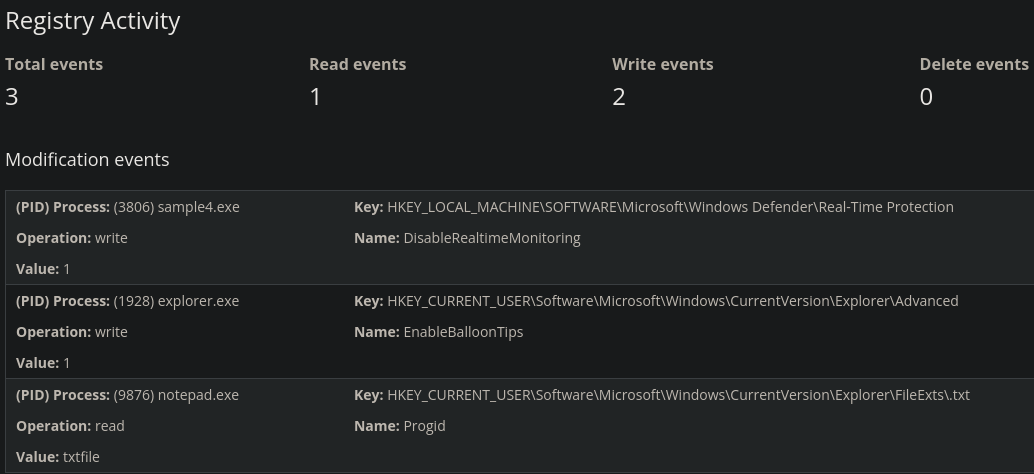
We will use the Sigma Rule Builder for this case. For Step 1 we choose Sysmon Event Logs and for Step 2 we pick Registry Modifications. In Step 3 we enter the values from the report.
If you google
att&ck DisableRealtimeMonitoring IDyou will see that its ID isT1562.002which falls under Defense Evasion with IDTA0005.
| Registry Key | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection |
|---|---|
| Registry Name | DisableRealtimeMonitoring |
| Value | 1 |
| ATT&CK ID | Defense Evasion (TA0005) |
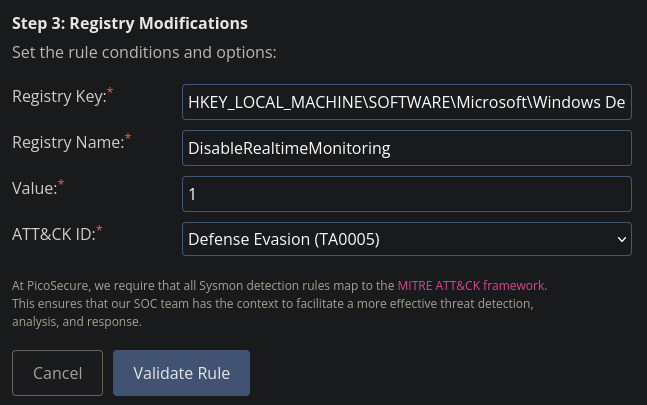
After validating the rule we get flag 4 in our inbox.
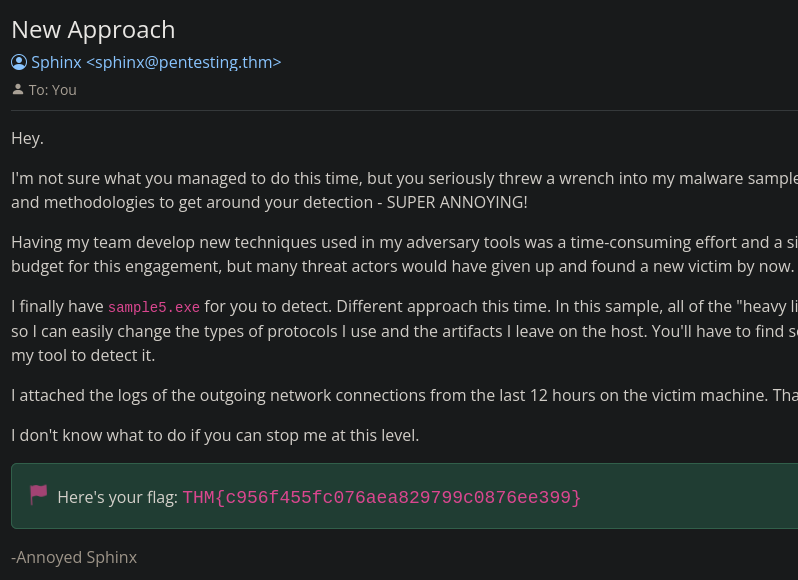
What is the fifth flag you receive after successfully detecting sample5.exe?
This time we have to focus on the logs to determine our countermeasure.
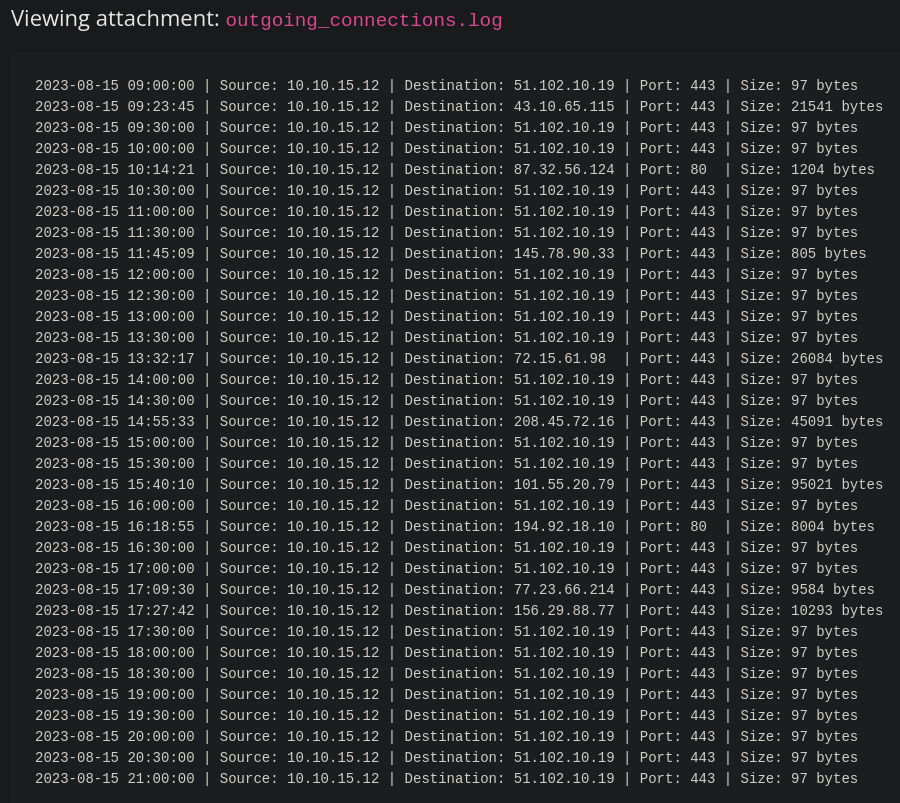
After paying close attention we notice some recurring traffic on the same port at regular intervals. Every 30 minutes there is some outgoing traffic of 97 bytes to IP 51.102.10.19. In the Sigma Rule Builder go to Sysmon Event Logs -> Network connections.
Because the threat actor can now change the artifacts we cannot rely of IP addresses, protocols, or port numbers. Also given the fact that the traffic occurs every 30 minutes we can assume that it uses an automated process probably via a C2 framework.
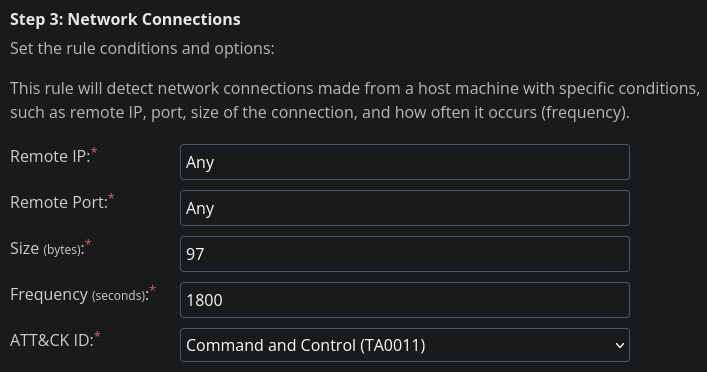
Using the values in the picture below we get the fifth flag.
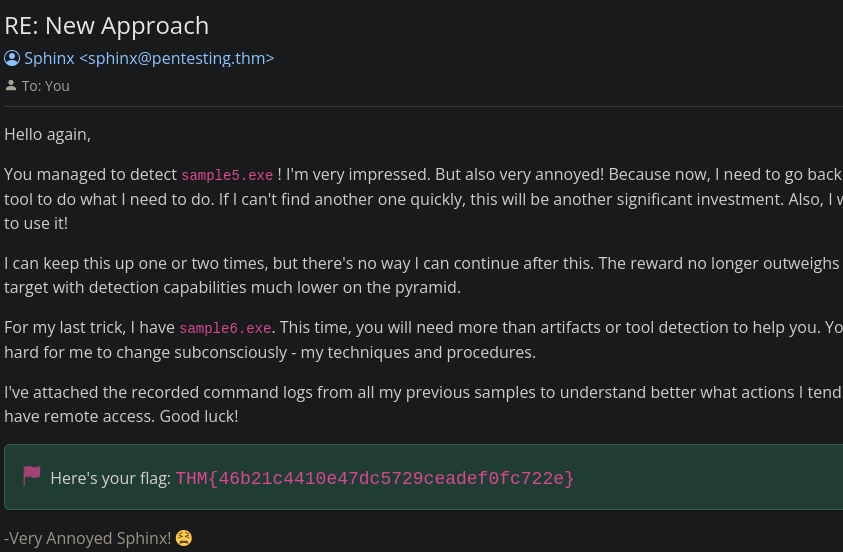
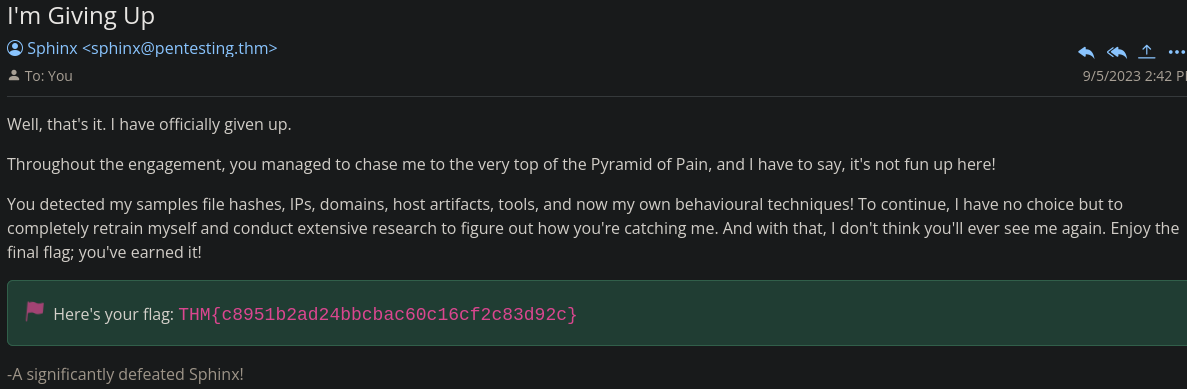
What is the final flag you receive from Sphinx?
We now need to make use of a commands log file.
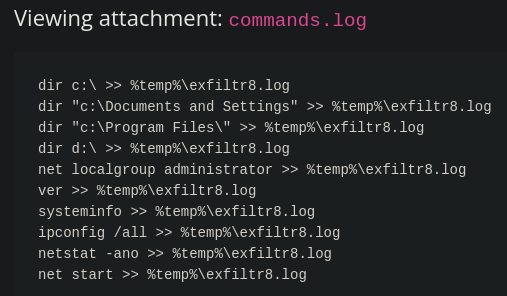
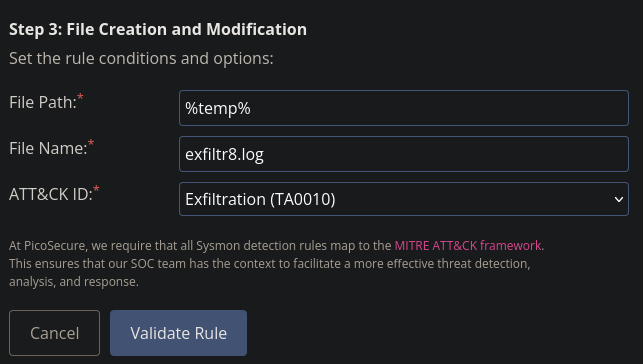
First we need to understand what those commands are doing. The commands suggest that the malware is performing reconnaissance and collecting information about the system, network, and user accounts. The output is stored in a log file (exfiltr8.log) in the temporary directory (%temp%), likely with the intention of exfiltrating this data to an external attacker.
The log file shows us that the temporary directory %temp% is always used in conjunction with a file named exfiltr8.log. So we should focus on that with our countermeasure.
Go to Sigma Rule Builder -> Sysmon Event Logs -> FIle Creation and Modification and use the options depicted below.
We then get the final flag.